The main function of the XACML framework is to enable the development of effective security policies across the enterprise, instead of implementing individual policies for each point of access. The goal is to promote a common language and interoperability between access control implementations by multiple vendors.
With the evolution of Web access management, many enterprises have adopted single sign-on systems where web-based authentication and coarse-grained authorization logic are separated from applications. The transition from RBAC to ABAC is inevitable as ABAC permits you to express a rich, complex access control policy more simply.
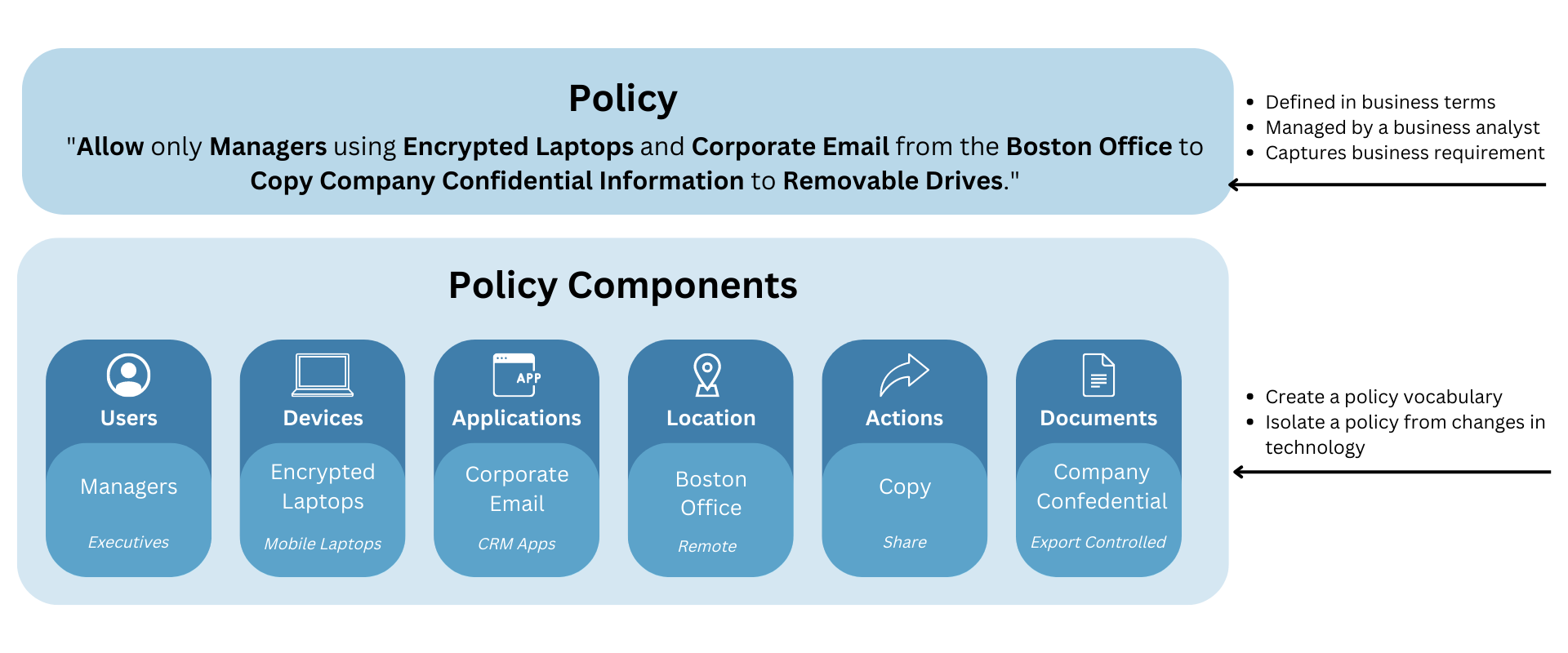
ABAC enhances RBAC by allowing an enterprise to extend existing roles using attributes and policies. Authorization decisions can be made based not only on a user’s role but also by considering other factors such as, who or what that user is related to. Therefore, by using a simple, easy-to-understand policy that considers the context of the user as well as what access he/she should have, access control becomes stronger and grows significantly in scope.
With ABAC, it also streamlines the management process for dynamic authorization. It removes the need to individually administer thousands or even hundreds of thousands of access-control lists and/or role and role assignments on a daily basis. Additionally, organizations do not need to deploy expensive and complex identity governance solutions. With ABAC, hundreds of roles can be replaced by just a few policies. These policies are managed centrally across all sensitive applications and systems, providing a single pane of glass over the “who, what, where, when, and why.” Centralized management makes it easy to add or update policies and quickly deploy them across the enterprise.
Furthermore, many enterprises are now developing custom access control solutions to meet the complex needs of their business. However, this can be costly and make it difficult to maintain quality service. With XACML, enterprises can avoid this dilemma entirely by adopting a commercial off-the-shelf (COTS) solution instead of building a custom one. XACML’s fine-grained, attribute-based access control policy language, policies can be modified without requiring code changes or application downtime. This enables organizations to react quickly to changes in business or regulatory environments, greatly increasing agility and flexibility, and enhancing overall data protection while greatly reducing cost. By centralizing access policies, it is not necessary to make software changes to individual applications and thus ensure consistent enforcement of policies across essential business applications – without requiring individual system administrators.

To comment on this post
Login to NextLabs Community
NextLabs seeks to provide helpful resources and easy to digest information on data-centric security related topics. To discuss and share insights on this resource with peers in the data security field, join the NextLabs community.
Don't have a NextLabs ID? Create an account.