Home | Intelligent Enterprise | Zero Trust Architecture
Zero Trust Architecture
Stay ahead with digitization, collaboration, and innovation
Home | Intelligent Enterprise | Zero Trust Architecture
Stay ahead with digitization, collaboration, and innovation
Zero Trust is a security framework that requires continuous authentication and authorization before granting access to resources or data. Designed to address threats that bypass traditional perimeter-based security, it focuses on protecting the data and resources within instead. It uses technologies such as identity and access management (IAM), segmentation, and encryption, to enforce security policies and limit access on a need-to-know basis.
Discover how how NextLabs simplifies the implementation of Zero Trust Architecture in alignment with DoD ZTA Reference Architecture for stakeholders
Learn how to secure an expanding digital core with Zero-Trust Data-Centric Security

Adoption of cloud computing and remote work has broadened the attack surface for organizations, leaving them vulnerable to cyberattacks.
haring data with different stakeholders across an extended enterprise increases the risk of breaches that would damage reputation and customer trust.
Many industries are subject to strict regulatory requirements around data access, such as HIPAA, PCI DSS, and GDPR.

Traditional security models are struggling to keep up with evolving risks, such as insider threats and supply chain attacks.
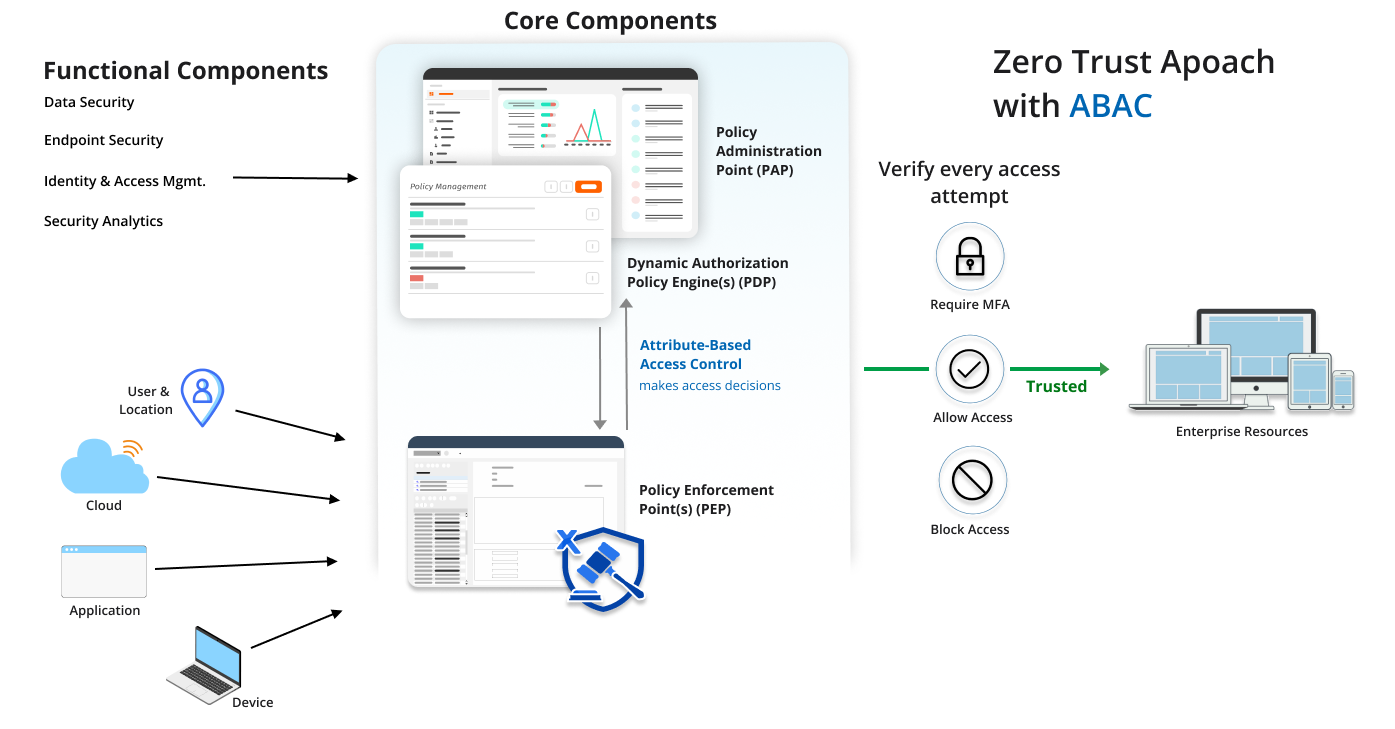
Never trust, always verify: All users, devices, and applications must be verified and authenticated before being granted access to any resources.
Least privilege access: Access should be granted on a need-to-know basis, and users should only be granted the minimum level of access required to perform their job functions.
Assume breach: Assume that an attacker has already compromised a secure resource and act accordingly to limit the attacker’s access and ability to move laterally within the network, system, application, or database.
Micro-segmentation: Segment resources into small, isolated zones to limit the spread of a breach and prevent attackers from moving laterally.
Continuous monitoring: All access attempts must be continuously monitored for signs of suspicious behavior, and appropriate action must be taken in response to any suspicious activity.
Contextual awareness: Security policies and access controls must be based on contextual awareness, such as the user’s role, device location, and sensitivity of the data being accessed.
CloudAz is a zero-trust policy platform that leverages a data-centric approach to provide continuous authentication and authorization of users, devices, and networks, safeguarding data beyond the network perimeter.
Users can easily author and oversee policies effectively with features such as approval workflows, version control and rollback, ensuring the system stays uncompromised.
Digital policies are evaluated in real time by the policy engine, which authorizes access based on contextual factors and user behavior. This ensures that organizational resources are constantly secured by a "never trust, always verify" strategy, regardless of their location or context.
All access attempts and authorization decisions are stored in a centralized log, where anomalous activity can be monitored, tracked and reported. This simplifies compliance reporting and enables the fine-tuning of security procedures.
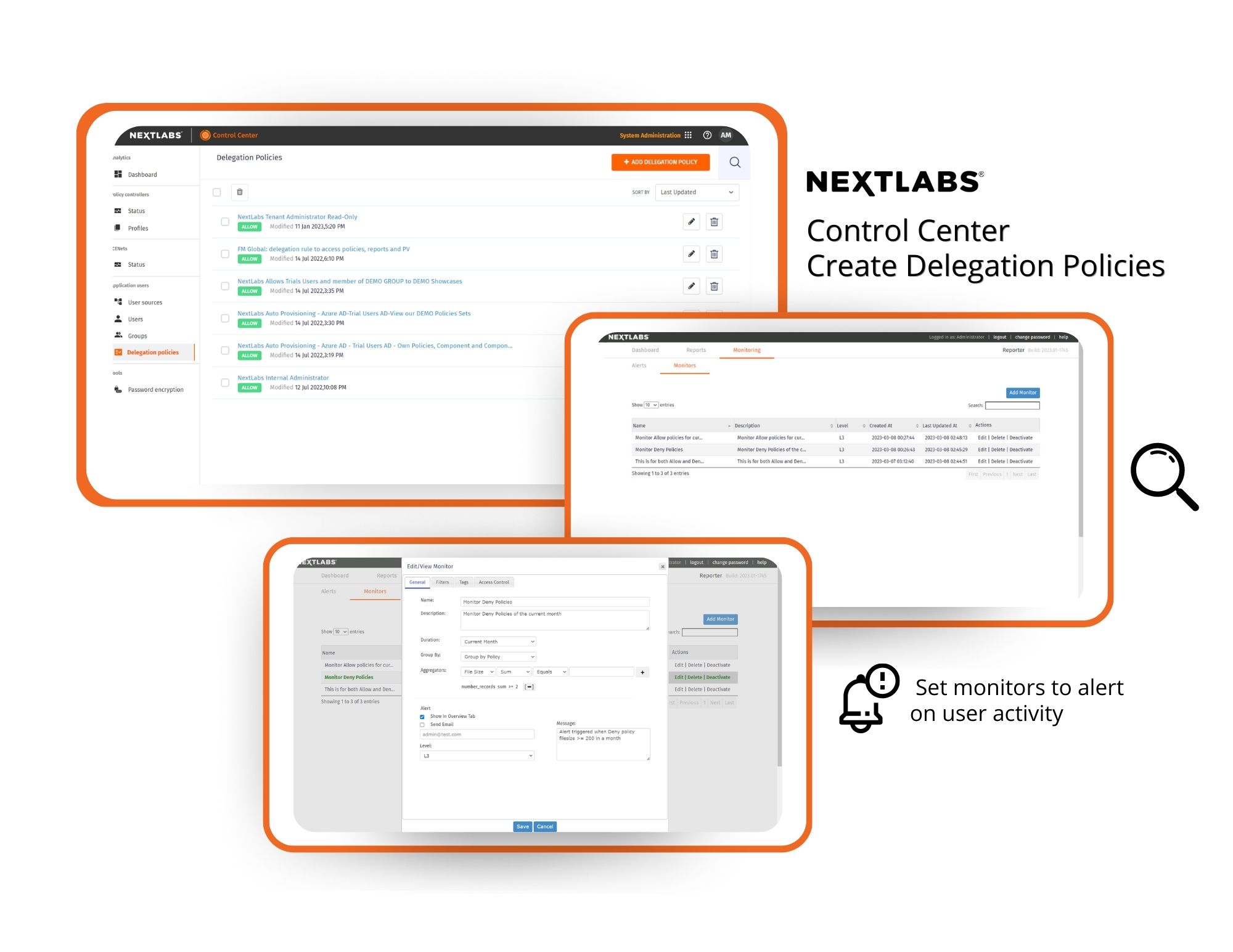
All access attempts and authorization decisions are stored in a centralized log, where anomalous activity can be monitored, tracked and reported. This simplifies compliance reporting and enables the fine-tuning of security procedures.
Quick Time-to-value & Deployment: Seamlessly integrated with enterprise applications and business processes, runs in cloud natively
Seamless User Experience: Simply policy authoring, business-friendly UI, no custom coding required
Robust Security & Audit: Strong monitoring and policy governance features ensure secure deployment without fear of compromise
Scalability & Performance: Highest performing zero-trust policy engine in the industry, with high availability and scalability

Implementing Zero Trust principles allows organizations to embrace digitization, collaboration, and innovation without sacrificing data security. By enforcing security policies consistently across organizations, and monitoring how sensitive data is being accessed and used, a zero trust solution secures migration to a more digitized and connected environment.
Zero Trust Data Centric Security
NextLabs® patented dynamic authorization technology and industry leading attribute-based zero trust policy platform helps enterprises identify and protect sensitive data, monitor and control access to the data, and prevent regulatory violations – whether in the cloud or on premises