Data Anywhere & Everywhere...
Intelligent Enterprises (IEs) need to protect data at the core anywhere and everywhere, in use, at rest, and on the move. An organization’s data protection is only as strong as its weakest link, so data security policies must be consistent across the entire enterprise and enforced dynamically at the time of data access to ensure they are always up to date. In addition, when collaborating with external partners organizations need to ensure that their data protection policies are still enforced. All these policies need to be kept up to date with any changes in factors that affect who is authorized to access protected data.


Implementing a ZTA
Explore the brochure on how to achieve a unified approach for access management and data security
Why Data-Centric Security?
Learn how BAE complies with electronic export regulations and protect IP while enabling and accelerating global collaboration
What is Dynamic Authorization?
Discover why enterprises need a Zero Trust strategy for secure global data access and a virtual workforce without compromising integrity
What is the Most Effective Way to Protect...
As data needs to be protected anywhere and everywhere, regardless of where it resides, whether on-premises, in the cloud, or in transit while ensuring that data remains protected independent of the device or network used to access it, security efforts to protect data should be focused on protecting data itself, instead of the systems or networks where data is kept. A conventional perimeter-based approach that focuses on securing access to a network is no longer sufficient to secure data because with global workforce, remote work, and move to cloud and hybrid environments, it is becoming too complex and costly to clearly defined perimeter between secure and insecure zones.
Since potential threats can originate either inside or outside of secure networks, every access and use of data must be verified and granted at the time of request. This is done on a need-to-know basis following least privilege principle, while monitoring access continuously with detailed logs to support audits and forensic investigations.
Protecting data comprehensively, whether it is at rest, in transit, or in use, across all the systems where data is stored, and used requires a multi-layered and policy-driven approach that incorporates a variety of data centric security enforcements and best practices which include identity management, access control, data masking and data segregation, encryption and digital rights management (DRM), and data loss prevention. . Data protection also needs to be applied dynamically in real-time based on policy, because as factors change that impact who and what is authorized to access a particular set of data, data security policies must evolve with the changes as well without manual intervention. Data security policies should be created based on data sensitivity and security requirements specifying how, when, where, and by whom data should be accessed, shared with, and protected from, and then applied to the appropriate set of data, regardless of whether it is in use, at rest, or in motion.
Zero Trust Data-Centric Security

Zero Trust Architecture (ZTA) assumes no perimeter and requires every access request to be verified, this suits well for the needs of protecting data everywhere and anywhere. The adaptable, policy-based, and identity centric approach of ZTA to security based on least privilege principle has received widespread corporate adoption and recognized by governments and regulatory bodies including US federal government, NIST, and many large corporations including Amazon, Boeing, Google, IBM, and Microsoft as the security architecture of the future. By adopting an approach that combines data centric security with zero trust architecture, organizations can ensure continuous protection of their data throughout its lifecycle and across all environments.
Zero Trust Data-Centric Security puts the data that needs to be protected at the center of an organization’s data security efforts. Policies are defined to protect the critical data, regardless of when, where, and how it is accessed. A Zero Trust approach ensures that every access request is validated before authorization is granted, protecting against threats that can originate inside or outside an organization’s secure network.
Key Components
01
Dynamic Authorization Policy Engine
A critical component to an effective Zero Trust Architecture because it allows policies to be evaluated and enforced at the time of the data access request
02
ABAC (Attribute-Based Access Control)
Policies help organizations cover different data security requirements without requiring the maintenance of separate roles and policies for each individual one.
03
Centralized Policy Definition & Management
Help ensure data protection policies are evaluated and enforced consistently. Centralized logging helps detect any potential threats and document compliance with policies.
04
Real Time Policy Evaluation & Enforcement
Ensures that access and authorization decisions always take any changes to policies or user attributes into account to protect data in use, where it is stored, and where it is accessed.
NextLabs Approach
NextLabs products enable organizations to protect their data, anywhere and everywhere. Our products use a Zero Trust data-centric approach to dynamically enforce data security policies, protecting data whether it is at rest, in use, or on the move. Data is protected within applications as well as in structured and unstructured data stores through NextLabs’ unified data security policy platform, providing a Zero Trust Architecture (ZTA) for organizations. Our dynamic authorization technology and real-time policy engine allows data access policies to be enforced at the time of access, wherever the data is being accessed.
Zero Trust Data Security
NextLabs Zero Trust Data Security is a comprehensive data centric security solution based on zero trust architecture to enforce access rights and protect structured and unstructured data throughout its entire lifecycle: at rest, in transit, and in use; regardless of where data resides – whether it is in application, file, file repository, or database on-premises, or in the cloud.
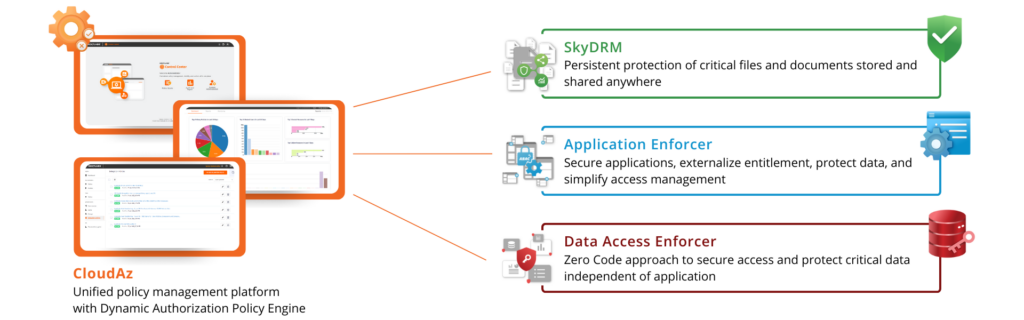
Core Functionalities

Dynamic Authorization and Zero Trust Architecture (ZTA)
Technology leader with 85+ patents and an official member of the NIST National Cybersecurity Excellence Partnership program since its inception.
Highest Performant and Most Scalable Policy Engine
The most mature & battle-tested policy engine in the industry processing greater than 10 billion authorization requests per year.
Comprehensive Data-Centric Security
Protect structured and unstructured data throughout its entire lifecycle: at rest, in transit, and in use; to ensure end to end secure data pipeline regardless of where data resides – whether it is in application, file, file repository, or database on-premises or in the cloud.
Externalized Authorization
Modify access and authorization policies centrally across the entire enterprise without having to make changes within each application.
Real-time Data Masking and Segregation
Data segregation and obfuscation policies that can be enforced dynamically at the time of the data access request ensures that protected data is only accessed by those who are authorized.
Native Application Integrations
Out-of-the-box, zero-code integrations with 100s of enterprise and business applications allow for quick and easy deployments and fast time to value.
Next Generation Technology
Cloud native and container-based unified policy platform and enforcers enable rapid multi and hybrid cloud deployment with the best time-to-value track record.

Run on any Cloud
Enterprises often have a combination of on-premises and across multiple cloud environments and need a single solution to protect data everywhere.
The NextLabs suite of products can be deployed anywhere, be it on-premises, in private cloud, or as a SaaS. Our products run natively on AWS, Azure, OpenShift and Google Cloud. With support for multiple deployment models, it gives you the freedom to choose the right cloud deployment strategy, whether it is hybrid or multi-cloud.
SaaS

Private Cloud

On-Premise
Consistent Policies
Whatever the environment, the NextLabs Zero Trust Data-Centric security suite of products allows organizations to apply data access policies to all of their data across the organization.
All Lifecycle Stages
Data is always protected, at rest, in use, and on the move, whenever and wherever it is being accessed.









