Home | Innovations | Technology
Technology
Never stop evolving – we’re always in pursuit of the next ground breaking technology
Home | Innovations | Technology
Never stop evolving – we’re always in pursuit of the next ground breaking technology
At NextLabs, our mission is to protect data anywhere and everywhere. We work relentlessly to develop technologies that empower enterprises to confidently tackle today’s data security challenges.
We created groundbreaking technologies, as listed below, based on next-generation Data-Centric Security and Zero Trust Architecture. NextLabs developed these technologies through the engineering of 90+ patents and 30+ pending patents, in the areas of dynamic authorization, attribute-based access control (ABAC), policy development & targeting, policy enforcement & optimization, access analytics, and next-generation digital rights management (E-DRM).
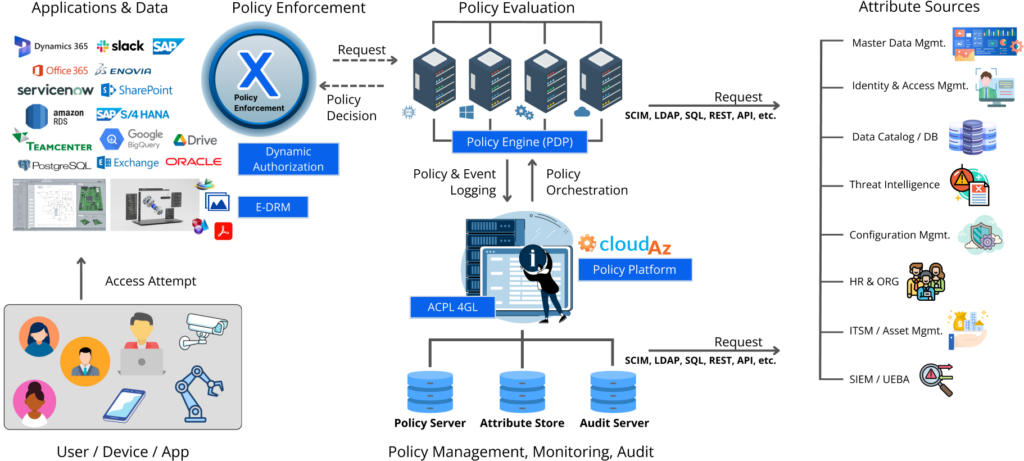
NextLabs Zero Trust Data Security is the result of our technologies and works seamlessly with enterprise IT infrastructures and vast cloud infrastructures. When a user, device, or application attempts to access an application or data, the policy engine (PDP) enforces the policy written by administrators through the use of dynamic authorization, Attribute-Based Access Control (ABAC), and enterprise digital rights management (E-DRM).
The policy being enforced stems from the zero trust policy platform (CloudAz), which provides a central location for administrators to author policies easily using wp, a non-procedural language that utilizes a natural language syntax similar to English, eliminating much of the complexities associated with other authoring policies.
Attributes from a variety of sources can be used with the zero trust policy platform to author policies. When an access attempt is made, the attributes of the user, device, or application are validated against the policy; if the attributes are aligned with the policy, the access attempt is granted. If the attributes are not aligned with the policy, the policy engine will deny access.
A non-procedural language that utilizes a natural language syntax like English designed to define context-aware security policies across applications and systems based on attribute-based access control (ABAC) principles. It is the underlying policy language of NextLabs CloudAz policy platform.
A software component built on a distributed architecture optimized to deliver high performance and highly scalable real-time and context-aware authorization decisions across application and data sources based on attribute-based policy.
The leading native zero trust multi-tenant policy platform with rapid policy development, robust governance, policy orchestration, and analytics functionality for managing authorization policies and provide continuous monitoring of data access activities across applications and services.
A multi-layered and policy-driven approach that focuses on safeguarding data itself by applying a variety of data security controls such as attribute-based access control, data obfuscation, data segregation, digital rights management (DRM), and data loss prevention directly to data in real-time.
The first Enterprise Digital Rights Management technology built-on Zero Trust Architecture to control access, secure sharing across enterprises, and protect usage of file and unstructured data of any types with security that stays with the file wherever it lives or travels to.
A technology framework that allow organizations to seamlessly apply security and compliance controls to existing applications without additional integration effort or customization, enabling rapid implementation of zero trust security model.
Typically, information and application access policies are hard coded into the application. That necessitates many months of coding effort to make any policy changes, which no longer fits with the speed of business today. Externalized Authorization Management externalizes access control decisions to a decision point that is decoupled from the application.
Enterprise Digital Rights Management (E-DRM) technology is designed to secure sensitive data from unauthorized access or theft by both internal and external parties. Learn more about how to implement E-DRM to ensure sustainable security protection for both your business and customer data.
In this article, we will explore the three key pillars of safeguarding AI, and how two powerful approaches, Zero Trust Architecture (ZTA) and Data-Centric Security, can be applied to protect AI systems.
Zero Trust Data Centric Security
NextLabs® patented dynamic authorization technology and industry leading attribute-based zero trust policy platform helps enterprises identify and protect sensitive data, monitor and control access to the data, and prevent regulatory violations – whether in the cloud or on premises

Join NextLabs’ Community
Login or create a NextLabs ID to receive unlimited access to white papers, case studies, and solution briefs.
NextLabs Community Members also receive newsletters, product updates, and other exclusive NextLabs news.