Microservices, otherwise known as microservices architecture, refers to an architectural approach that is composed of many small services which are loosely coupled and independently deployed.
This is unlike monolithic architecture, which is a traditional model that is built as a single service with all its processes tightly coupled. A small change made to any section of a monolithic application’s code would affect the entire system. Because of this, the code base grows and makes any modification to the features more complex. With microservices architecture, applications can be scaled easily and be more agile.
Characteristics of Microservices
Microservices are composed of multiple services that have their own unique database and data management model. The services are autonomous in which any updates to the existing service can be made without affecting the functionality of other services. Individual services use well-defined Application Programming Interface (API) to communicate with one another.
Each service is built to specialize in addressing a specific problem. The services may be written in different programming languages and use different data storage techniques causing services not have to share the same technology stack or framework, allowing the development of systems to be flexible and scalable.
Why do organizations need microservices?
According to a survey by McKensey, more organizations today are transforming their business models by adopting digital technologies to meet new demands and to be economically viable. As organizations are taking the step towards digital transformation, one of the most common transitions would be from an on-premises server to cloud. While moving to cloud, microservices are a need for cloud native applications.
So, what are some reasons that organizations might consider microservices as a need for digital transformation?
With microservices, only the service needed for the task will be activated. This reduces the need for the whole IT infrastructure to be deployed all the time, thus reducing the complications and cost of growth. In addition, more resources can be allocated to innovation as it enables teams to develop and test services in the application without affecting the other services. This allows organizations to manage and scale the applications easily, which helps companies easily modernize their IT infrastructure.
Companies like Uber have adopted this kind of architecture to overcome the challenges of a monolithic architecture. Uber’s platform had encountered challenges and complexity to efficiently make modifications, fix bugs and scale with the monolithic architecture. To overcome this, Uber had moved to a microservices architecture where they built individual microservices for services such as driver management, passenger management and trip management.
Benefits
- Agility. Microservices are deployed independently which enables the management of the service to be simpler – modifying a service (I.e., update, fixing a bug) can be done without redeploying the entire application.
- Scalability. Individual service is scaled independently to meet the demand for the application feature it supports, without scaling the entire application.
- Technological Freedom. A suitable mix of technologies is chosen for each service, to address specific problems.
- Resilience. Microservices allow services, which are autonomous, to be more resilient to failure when a service is down. The affected service will be isolated, and this will not cause the entire application to crash.
- Reusability. A service that provides a certain function can be a building block for another feature. Since codes and data are not shared, more features can be added easily.
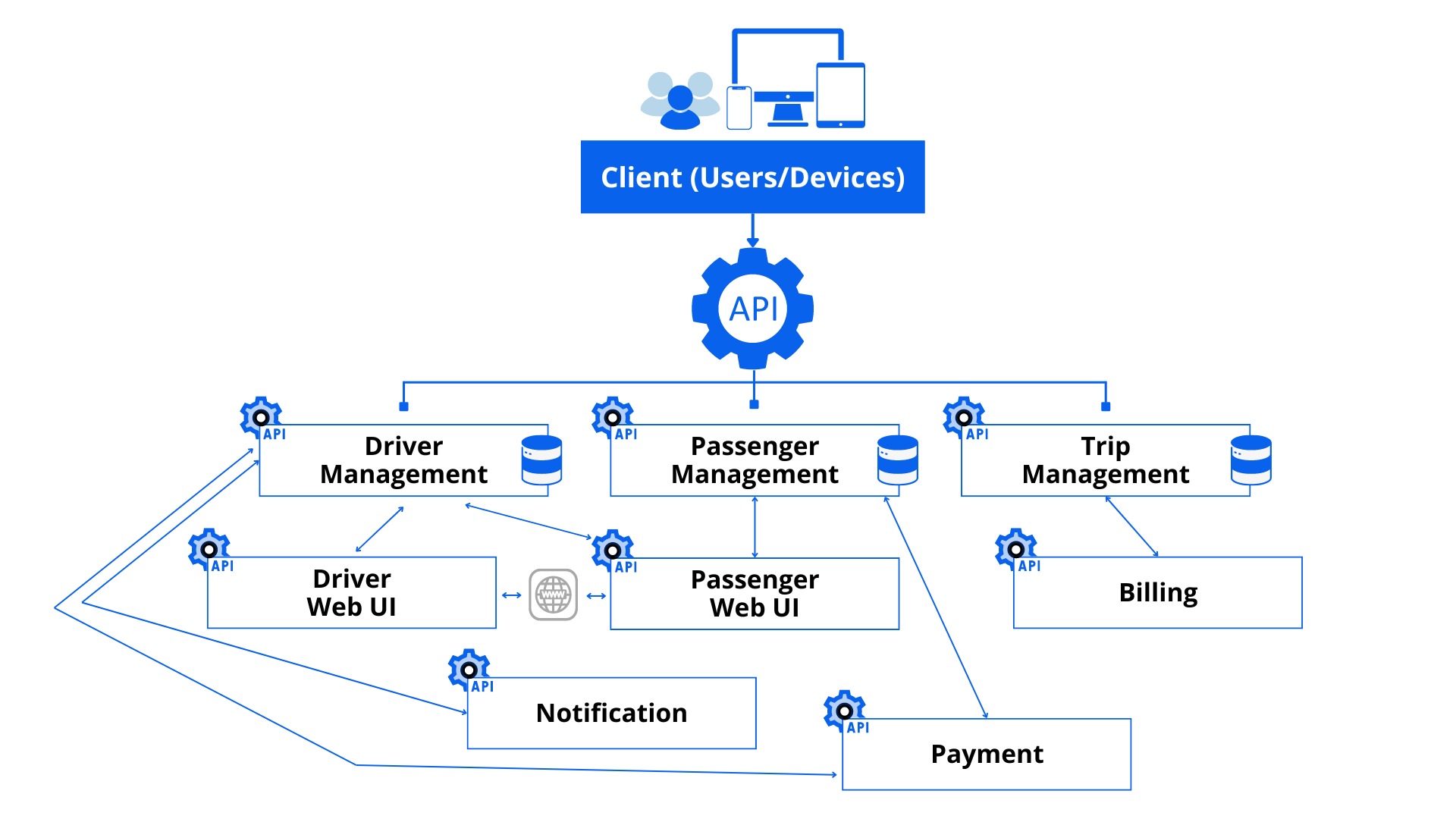
Building this kind of architecture does come along with challenges such as data integrity. Code and data schemas could be inadvertently disclosed, or internal implementation details could be leaked through APIs. Therefore, it is increasingly important to prevent sensitive data from being exposed through APIs and microservices.
How to secure microservices
Securing microservices involves implementing several security measures at various levels of the architecture to protect against unauthorized access, data breaches, and other security threats. Here are some steps you can take to secure your architecture:
- Implement access control: Microservices should only be accessible to authorized users or services. Access control measures like authentication, authorization, and attribute-based access control (ABAC) can be used to ensure that only authorized users or services can access the microservices.
- Implement monitoring and logging: Monitoring and logging are crucial to analyze and detect any abnormal behavior or security threats in the environment.
- Implement container-level security: Containerization helps to isolate microservices so that it is easier to deploy and manage them. In the situation where there is a malicious code affecting a microservice, it can be isolated to prevent other microservices from being affected.
- Perform security testing: Conduct regular security testing to identify potential vulnerabilities and weaknesses in the security measures.
By following these best practices, organizations can ensure that their microservices are secure and protected against potential security threats.
To understand more on how to secure microservices, watch this episode of NextLabs Cybersecurity Expert Series.
Alexandru Ghinea shares his insights on securing microservices to prevent cybersecurity attacks. He covers what a microservices architecture looks like, what threats this architecture may pose, and how to implement a data-centric security (DCS) approach with this architecture.
Alexandru Ghinea is a DevOps Engineer for the Societe Generale. Alexandru has over 8 years of experience in the cybersecurity field.
To comment on this post
Login to NextLabs Community
NextLabs seeks to provide helpful resources and easy to digest information on data-centric security related topics. To discuss and share insights on this resource with peers in the data security field, join the NextLabs community.
Don't have a NextLabs ID? Create an account.