SkyDRM
Persistently protect files stored and shared anywhere
Protection Across the Extended Enterprise
SkyDRM is designed to protect data as it moves and is shared across today’s extended enterprise. Any file type can be protected and accessed from any device to ensure secure collaboration. Users can access protected files through a web browser, mobile clients, or their native applications.


SkyDRM Brochure
Explore the brochure on how to persistently protect files stored and shared anywhere
Bajaj Customer Story
Learn how Bajaj ensures secure data access, authorized sharing, real-time anomaly alerts, and compliance reporting
SkyDRM Data Sheet
Learn how SkyDRM protects sensitive documents flowing through internal and external business processes
Protecting Information
Throughout its Lifecycle
01
Collaboration: An Essential
Enterprises must embrace a collaborative approach to data sharing to operate worldwide and foster partnerships.
02
Need To Share Vs. Protect
The requirement for collaboration calls for the need to balance between sharing information and safeguarding sensitive assets.
03
Securing Shared Data
As more collaboration tools become available, it raises the challenge of protecting data once it is shared beyond the source.
04
Extended Sharing
External collaboration exacerbates the risk of IP leakage, especially when operating within a global supply chain.
So how do organizations safeguard confidential information (trade secrets & IP) from wrongful disclosure throughout its lifecycle and across the extended enterprise?
The Solution:
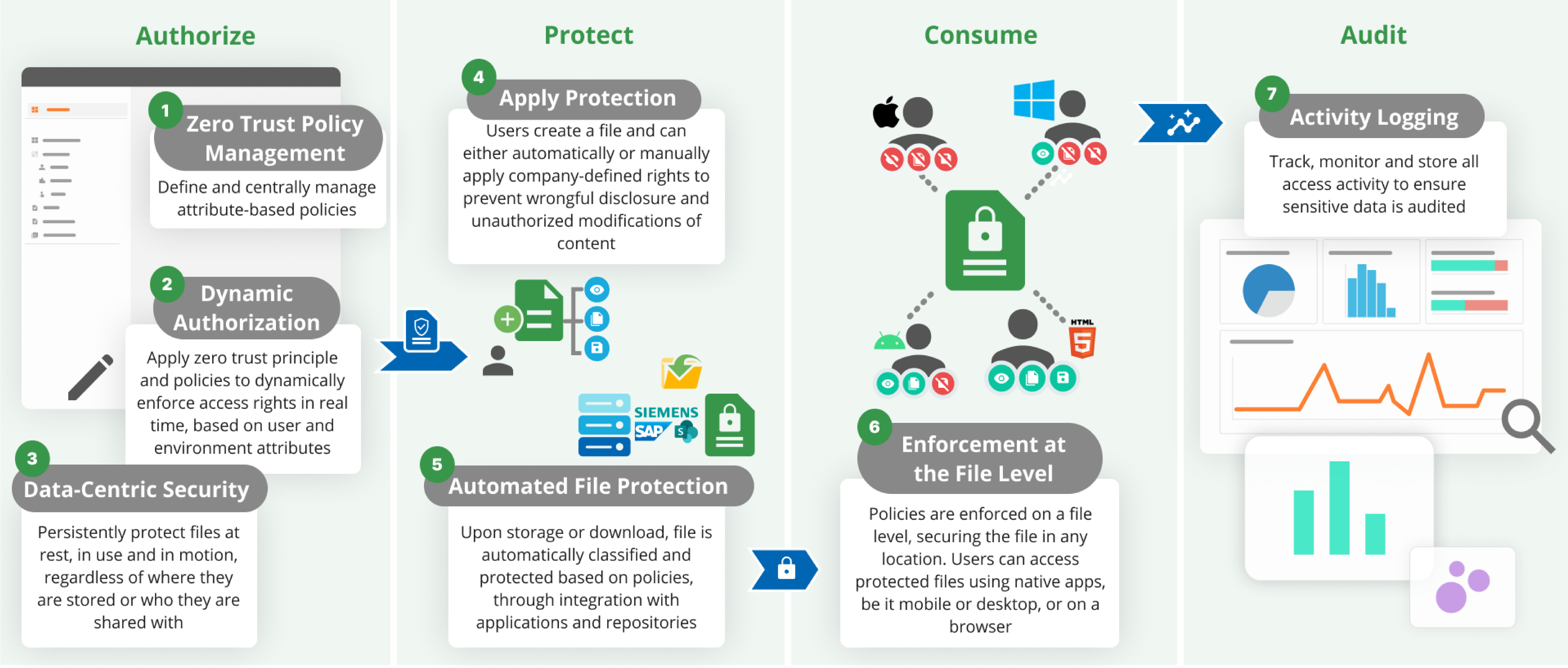
Enterprise Digital Rights Management Solution that uses zero trust principle to automate persistent protection of sensitive information.

Enterprise Digital Rights Management Solution
The solution persistently protects files across the information cycle using attribute-based policies. Attribute-based policies dynamically grant permissions for specific actions, such as viewing, editing, copying, forwarding, printing, and extracting content, based on the recipient’s identity.
Automation
Automates data security, compliance procedures, and internal controls to enhance competitiveness and agility.
Integration
Out-of-the-box integration with apps, microservices, and business processes without disruptions.
Enforcement
Detects, alerts and applies preventive controls to enforce policy in real time.
Deployment
Runs in cloud natively, deploys using containers in a hybrid and multi-cloud environments.
Introducing skyDRM
Protect data at Rest & In Motion
NextLabs’ Application Enforcer augments an application’s underlying security model, providing an extra layer of controls for organizations with extensive security and compliance requirements, without the need for custom coding.
Externalized Authorization
Modify authorization policies without having to make any code changes to the application itself.
Enforce Least Privilege Access
Uses ABAC to enforce the principle of least privilege, ensuring apps and data are accessed only by authorized entities.
Leverage Data Classification
Automatically identifies sensitive data types based on the app's underlying data model, organizes data into relevant categories.

Leverage Data Classification
Automatically identifies sensitive data types based on the app's underlying data model, organizes data into relevant categories.
Collects Access Activity Across Apps
Discerns and collects relevant data to facilitate centralized correlation & detection of anomalous activity.
Native Application Integration
Understands identity system, object & security model of apps, for easy deployment & seamless user experience
Benefits
- Protect sensitive data – Control access to sensitive data based on attributes such as data classification, environmental information, user roles, metadata and location.
- Improve business agility – Works natively with application and externalizes authorization, slashing application development time and automating change management processes.
- Improve time-to-market and reduce costs – Eliminates the need to implement and maintain costly customizations to meet security, compliance, and governance requirements.
- Streamline Compliance – Automates the process of auditing authorization and data access to demonstrate compliance to auditors, regulators, and customers.

Integrate Seamlessly
Application Enforcer product line provides support for the following ecosystems:

SAP ERP, SAP HANA, SAP BW/4HANA

NX, Teamcenter, SolidWorks

Word, PowerPoint, Excel

Google Drive, OneDrive, SharePoint, Box, Dropbox

ProjectWise, Microstation

AutoCAD, Inventor

SolidWorks, CATIA

Windchill, Creo
SkyDRM Brochure
Explore the brochure on how to persistently protect files stored and shared anywhere
SkyDRM Data Sheet
Learn how SkyDRM protects sensitive documents flowing through internal and external business processes
A New Approach to DRM
Discover a new approach to protect enterprise data from unauthorized access, use, and distribution





