In today’s increasingly digital, globalized business environment, enterprise access entitlements and data security needs demand a policy-driven approach to automate and secure access to many diverse applications, data stores, systems, and topologies. These applications run on servers, desktops, laptops, mobile devices – both online, offline, and on the Internet as software services. Therefore, custom built authorization and entitlement solutions that only provide static and role-based policy evaluation for a specific application no longer have the required capability and reach to meet current cybersecurity requirements. This is where a zero-trust policy engine comes in. A zero-trust policy engine allows your organization to adapt to the ever-changing needs of today’s business requirement by providing the flexibility to make changes to access rights and data security needs on the fly via policy without complex customization and manual procedures.
Role in Zero Trust Architecture & Zero Trust Security
A policy engine is an essential component of the Zero-Trust Architecture (ZTA), which has gained popularity in recent years as a security model that trusts no user or device by default. In a Zero-Trust environment, security policies are based on the principle of least privilege, where users and devices are only granted access to the resources, they need to perform their duties. The Policy Engine works hand in hand with Zero-Trust policy management (ZTPM) to enforce policy and grant access to the enterprise resources. ZTPM involves defining and enforcing policies that ensure access to sensitive data and critical systems is only granted to authorized users and devices. ZTPM also includes the creation, enforcement, and continuous monitoring of access policies, as well as interfacing with the identity and access management (IAM) systems.
Read the white paper to dive into the crucial role of the policy engine within a ZTA—its function, underlying architecture, benefits, and the challenges associated with its implementation—and specific business use cases across various industries, including how the engine fits within NextLabs’ data security solution.
What is a Policy Engine?
A policy engine is a software component or system that is responsible for evaluating and enforcing policies or rules within an organization or application. It acts as a decision-making mechanism, interpreting policies and determining whether specific actions or behaviors comply with those policies.
A policy engine typically receives inputs or events, such as user requests, system events, or data updates, and applies predefined rules or policies to make decisions or take appropriate actions. These policies can cover a wide range of domains, including security, access control, compliance, governance, business rules, or any other set of guidelines that need to be enforced. The policy engine then evaluates the inputs against the defined policies and produces outcomes or decisions based on the rules specified. It can allow or deny access, trigger automated actions, provide recommendations, or perform any other action according to the policies in place.
A Dynamic Authorization – also known as attribute-based access control (ABAC) – policy engine is a specialized type of policy engine that evaluates policy in real-time based on attributes associated with entities within a system. Dynamic Authorization policy engines enable fine-grained access control decisions by allowing complex policies to be defined based on combinations and relationships among attributes. This type of policy engine evaluates access requests by matching the attributes associated with the subject, resource, and environment against the defined policies.
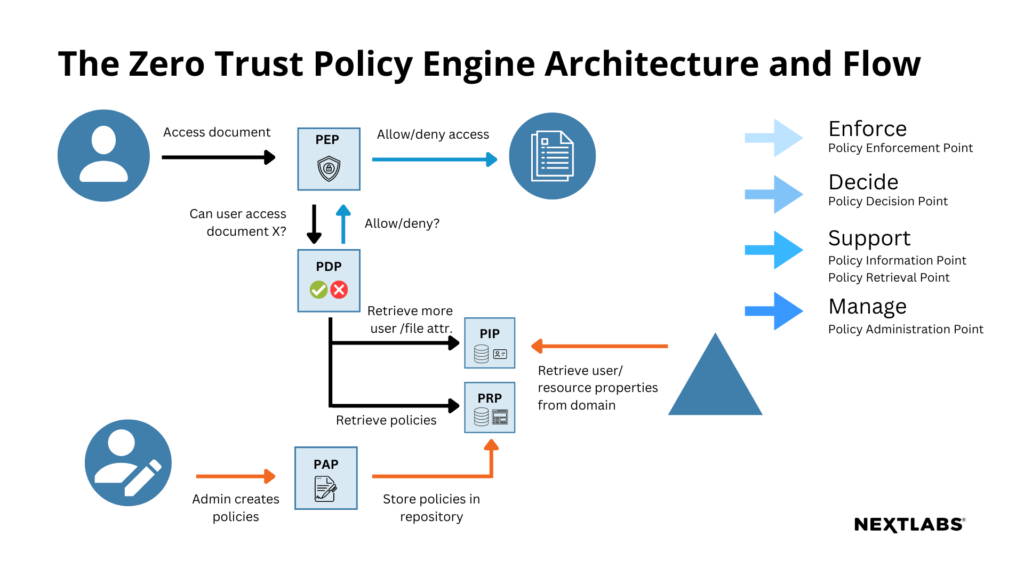
Based on this evaluation, the engine determines whether the requested access should be granted or denied. Beyond just controlling access to application data, files and documents, the policy engine can enforce granular policies to segregate and obfuscate data as needed.
How does a Policy Engine Work?
A policy engine follows a specific set of steps to evaluate and enforce policies. Below is a general overview of how a policy engine typically works:
- Policy Definition: Policies are defined and configured within the policy engine or policy server for the policy engine. This involves specifying rules, conditions, and actions that govern the behavior or decisions to be made. Policies can be expressed in a policy language, rules language, or a structured format specific to the policy engine.
- Input Acquisition: The policy engine receives inputs or events that require policy evaluation. These inputs can be user requests, system events, data updates, or any other relevant information that triggers policy enforcement.
- Contextual Information Gathering: The policy engine collects relevant contextual information related to the input or event. This may include attributes associated with the subject, resource, environment, or any other relevant information required for policy evaluation – for example user status, data classifications, and the device user is accessing the data from.
- Policy Evaluation: The policy engine evaluates the inputs and contextual information against the defined policies. It applies the rules and conditions specified in the policies to make decisions or determine appropriate actions. This evaluation process typically involves matching attributes, applying logical operators, and considering rule priorities or precedence.
- Decision Making: Based on the policy evaluation, the policy engine decides or determines an action to be taken. This decision can involve granting or denying access, triggering automated actions, providing recommendations, or any other response specified in the policies.
- Action Execution: If the policy engine determines that an action needs to be taken, it triggers the execution of the specified action or actions. This may involve modifying data, sending notifications, invoking external services, enforcing access control, or any other relevant operation based on the policies.
- Logging and Auditing: The policy engine typically records the decisions made and actions taken for auditing and compliance purposes. It maintains a log or audit trail that captures the policy evaluation process and the outcomes.
- Policy Updates and Management: The policy engine allows for policy updates and management. This includes modifying existing policies, adding new policies, or removing obsolete policies. It provides mechanisms to maintain and manage the policy set efficiently.
Key Benefits of a Policy Engine
Policy engines offer several key benefits in the context of managing and enforcing policies. Here are some of the major advantages:
- Centralized Policy Management: Centrally manage, define, update, and maintain policies in a single location. This streamlines the administration process and ensures consistency across the entire system or application.
- Flexibility and Agility: Policies can be easily modified or updated without making significant changes to the underlying system or application. This flexibility allows organizations to adapt quickly to evolving business requirements, regulatory changes, or new security needs.
- Fine-Grained Access Control: Policy engines enable fine-grained access control by considering multiple attributes and conditions. Organizations can define policies based on various factors such as user roles, resource classifications, time of day, location, and more. This granular control enhances security and helps enforce the principle of least privilege.
- Dynamic Policy Evaluation: Policy engines support dynamic policy evaluation, considering real-time or contextual information during access control decisions. For example, policies can consider the current environmental conditions or user context when granting or denying access. This dynamic evaluation enhances security and allows for adaptive access control.
- Consistent Policy Enforcement: With a policy engine, policies can be enforced consistently across different systems or components. Centralized policy management ensures that policies are uniformly applied, avoiding discrepancies or inconsistencies that may arise when policies are implemented independently.
- Auditing and Compliance: Policy engines often provide auditing and logging capabilities. They record policy evaluation results, decisions made, and actions taken, creating an audit trail for compliance purposes. Auditing helps organizations demonstrate compliance with regulations, industry standards, or internal governance requirements.
- Separation of Policy and Application Logic: Policy engines facilitate the separation of policy logic from application or system logic. This separation enhances modularity and maintainability as policies can be managed independently and applied to various systems or applications without tightly coupling them.
- Reusability and Scalability: Policies defined within a policy engine can be reused across different systems or applications, eliminating the need to duplicate policy logic. This reusability simplifies policy management and reduces development effort. Additionally, policy engines can scale to handle large volumes of policy evaluations efficiently, ensuring performance in complex and dynamic environments.
Common Applications of Policy Engine
Policy engines have numerous common use cases across various industries and domains. Here are some of the most common applications of policy engines:
- Access Control and Authorization
- Governance, Risk, and Compliance (GRC)
- Workflow and Process Automation
- Data Security and Privacy
- Resource Allocation and Optimization
- Internet of Things (IoT)
- Service Level Agreement (SLA) Enforcement
- Adaptive User Interfaces
Overall, policy engines provide organizations with a powerful tool for managing policies effectively. They offer centralized control, flexibility, fine-grained access control, and the ability to adapt to changing requirements, contributing to enhanced security, compliance, and operational efficiency.
NextLabs’ Solution
NextLabs’ CloudAz is a unified policy platform with real-time enforcement that centralizes administration and employs a zero-trust principle to enforce data-centric security (DCS) measures and compliance in real time, by automating least privilege access and securing applications and data.
CloudAz’s patented, dynamic authorization policy engine uses real-time contextual information to evaluate conditions in policy set to make authorization decision. These conditions are based on user, environment, and resource characteristics (“attributes”), which are evaluated in real-time to determine what permission a user or subject should be granted to applications, APIs / microservices, business transactions, and data. This policy engine is able to account for changes in user status or changes in the resource. For instance, if an employee moves to a different department within the company, no new policy needs to be created since policies are evaluated against the latest set of attributes without the need for manual intervention.
CloudAz can be deployed anywhere, be it on-premises, in private cloud, or as a SaaS. CloudAz runs natively on AWS, Azure, OpenShift and Google Cloud. With support for multiple deployment models, it gives you the freedom to choose the right cloud deployment strategy, whether it is hybrid or multi-cloud. With the ability to create new instances across multiple landscapes – set up development, test, and production environments can be done quickly. Policies can be transported between cloud and on-premises deployments, ensuring consistent policy enforcement across all environments.
Key Benefits of NextLabs’ CloudAz
- Unify & Modernize IT: Streamline IT infrastructure, unify application and business services under a shared services model, expedite system consolidation and eliminate security silos, accelerate cloud adoption without compromising security coverage and total cost of ownership.
- Improve Business Agility: Accelerate time to market and enhance competitive advantage through automation and simplified change management; easily incorporate new business models without code changes and application downtime.
- Enhance Cybersecurity: Prevent data leakage and cyber-attacks by automating least privilege access to eliminate implicit trust and safeguard data across business critical applications (e.g. SAP, Siemens, Microsoft, ServiceNow, Oracle), whether the data is at rest or on the move.
- Increase Collaboration: Safeguard trade secrets and sensitive information to ensure secure data sharing and accelerate collaboration through central access control and data segregation policies.
- Ensure Compliance: Ensure compliance with regulations such as GDPR, ITAR, SOX and EH&S, simplify audit processes with centralized logging and reporting of all data access activity and authorization decisions.





