Home | Intelligent Enterprise| Zero Trust Architecture | Zero Trust Data Security: Explained
Organizations adopt Zero Trust security models because traditional security models that rely on a perimeter-based approach are no longer sufficient to protect against the increasing sophistication and frequency of cyber attacks. Zero Trust is designed to address the limitations of traditional security models by assuming that all access attempts are potentially malicious, even if they are from within the organization’s network. The following are the key drivers for organizations adopting Zero Trust:
- Protect against data breaches: Data breaches can have significant financial and reputational consequences for organizations. Zero Trust helps to reduce the risk of data breaches by limiting access to sensitive data and continuously monitoring all access attempts for signs of suspicious activity.
- Secure access: The COVID-19 pandemic has accelerated the adoption of remote work, which has increased the attack surface for organizations. Zero Trust helps to secure remote access by ensuring that all devices and users are verified and authenticated before being granted access to data or other resources.
- Compliance: Many industries are subject to strict regulatory compliance requirements, such as HIPAA, PCI DSS, and GDPR. Zero Trust can help organizations to meet these compliance requirements by ensuring that only authorized users have access to sensitive data.
- Prevention of lateral movement: Once a cyber attacker gains access to a secure network, system, or application, they can move laterally within that resource to find valuable data. Zero Trust can help prevent lateral movement by segmenting a network, system, application, or database into smaller, isolated zones and limiting access to only authorized users and devices.
- Evolving threat landscape: Cyber threats are constantly evolving, and traditional security models may not be able to keep up with the latest threats. Zero Trust is designed to be adaptive and able to evolve with the changing threat landscape, ensuring that organizations are better protected against the latest threats.
By adopting Zero Trust, organizations can better protect their systems, data, and resources from cyber threats. Zero Trust helps organizations to reduce their attack surface, minimize the impact of a breach, and improve their overall security posture by continuously verifying the identity of users and devices and evaluating the risk profile of access requests.
Zero Trust Principles
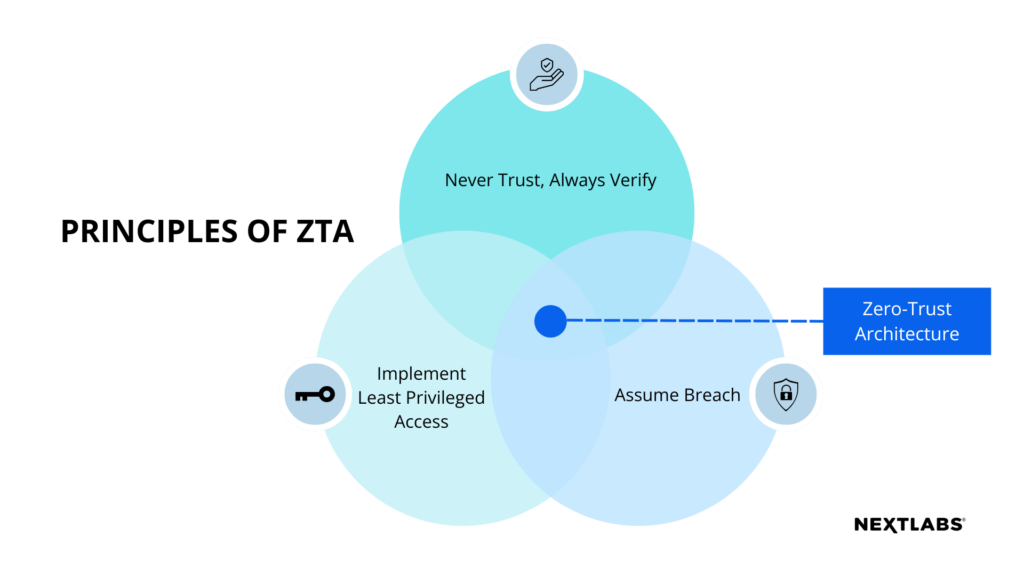
Zero Trust principles are a set of security concepts that aim to protect an organization’s systems, data, and resources by assuming that all access attempts are potentially malicious, even if they are from within a secure network, resource, or application. The following are the key principles of Zero Trust:
- Never trust, always verify: All users, devices, and applications must be verified and authenticated before being granted access to any resources.
- Least privilege access: Access should be granted on a need-to-know basis, and users should only be granted the minimum level of access required to perform their job functions.
- Assume breach: Assume that an attacker has already compromised a secure resource and acts accordingly to limit the attacker’s access and ability to move laterally within the network, system, application, or database.
- Micro-segmentation: Segment resources into small, isolated zones to limit the spread of a breach and prevent attackers from moving laterally.
- Continuous monitoring: All access attempts must be continuously monitored for signs of suspicious behavior, and appropriate action must be taken in response to any suspicious activity.
- Contextual awareness: Security policies and access controls must be based on contextual awareness, such as the user’s role, device location, and sensitivity of the data being accessed.
By following these principles, organizations can better protect their systems, data, and resources from cyber threats. Zero Trust principles help organizations to reduce their attack surface, minimize the impact of a breach, and improve their overall security posture by continuously verifying the identity of users and devices and evaluating the risk profile of access requests.
Data-Centric Security Principles
Data-centric security (DCS) principles are a set of principles that are focused on protecting an organization’s sensitive data at the data level, as opposed to simply relying on traditional perimeter-based security measures. These principles aim to ensure that the organization’s sensitive data is secured at all times, supporting data access security regardless of its location or how it is being accessed. The following are some of the key principles of data-centric security (DCS):
- Data Classification: All data must be classified according to its sensitivity, and access must be granted on a need-to-know basis.
- Persistent Data Encryption: Sensitive data must be encrypted both in transit and at rest to protect it from unauthorized access.
- Data Obfuscation: Sensitive data must be masked or redacted, or replaced with a token, which can be used for certain processes without exposing the underlying data to unauthorized access.
- Data Segregation: Data should be segmented as fine-grained as possible, so that access to data can be limited to the minimum necessary for each access request.
- Data Authorization and Entitlement: User entitlements to data must be granted on a need-to-know basis and only after the identity of the user and device has been verified and the risk profile of the access request has been evaluated.
- Data Loss Prevention (DLP): Measures must be taken to prevent data loss, such as preventing unauthorized copying, printing, or emailing of sensitive data.
Data-centric security (DCS) principles help organizations to better protect their sensitive data by focusing on securing the data itself, rather than just the perimeter around it. By following these principles, organizations can reduce their attack surface, minimize the impact of a breach, and improve their overall security posture by continuously verifying the identity of users and devices and evaluating the risk profile of access requests.
Applying Zero Trust Principles to Data-Centric Security
Zero Trust and Data Centric security can be complementary approaches to security. Zero Trust can help to limit access to sensitive data, while Data Centric security can help to protect the data itself. By combining the two approaches, organizations can create a comprehensive security strategy that provides both network-level and data-level protection, helping to improve their overall security posture.
A Zero Trust Data Security approach allows organizations to do the following.
- Implement Least Privileged Access and Need-to-Know by defining and enforcing security policies that provide fine-grained data access and authorizations to allow users to view and use all the data they should be able to access and nothing more.
- Segregate Data for export and regulatory compliance by virtually segmenting shared resources.
- Secure Collaboration with Persistent Data Protection that stays with the data and protects it at rest in databases, in use within applications, and on the move when it is shared.
- Unify Access Control with Attribute-Based Access Control (ABAC), eliminating the need for large numbers of groups or roles and replacing them with a small number of policies where user, data, and environmental attributes are evaluated dynamically at the time of the access request.
- Externalize Access Management and Eliminate Security Silos so that security policies are enforced consistently across the entire organization.
With Zero Trust Data Security, organizations can better protect their sensitive data from cyber threats and ensure that access remains in compliance with security policies. The combination of Zero Trust and Data-Centric Security (DCS) principles help organizations to reduce their attack surface, minimize the impact of a breach, and improve their overall security posture by continuously verifying the identity of users and devices and evaluating the risk profile of access requests.
Zero Trust Data Security Solution Use Cases
The following are some of the common business applications of Zero Trust Data Security.
- Modernization – With Zero Trust Data Security enterprises can keep data secure during system modernization projects by providing centralized authorization for legacy and new applications.
- Segregation of Duties (SoD) and Compliance – Global enterprises often have many different and overlapping regulations that they need to comply with. Zero Trust Data Security allows organizations to enforce segregation of duties to ensure no violations of applicable regulations, including GDPR, SOX, ITAR, FDA, etc. while automating controls and the audit process.
- ERP Consolidation – Enterprises are driven to consolidate multiple existing ERP instances into a single global instance for all of the efficiencies this brings. Zero Trust Data Security allows organizations to protect critical data while consolidating those existing ERPs into a single global instance.
- M&A, JVs, Divestitures – Enterprises in the process of mergers, acquisitions, divestitures or joint ventures can keep sensitive data safe while integrating new businesses or splitting off businesses from parent companies. This allows them to comply with M&A, JV, or divestiture agreements while having quicker implementation and lowering the security risk by segregating and partitioning data on existing systems.
- Cybersecurity – Cybersecurity threats are always evolving, and organizations must continually adapt their defenses to counter the latest threats. Zero Trust Data Security allows enterprises to reduce cybersecurity risks and implement the best practices as defined in the NIST Cybersecurity Framework (CSF). This helps facilitate data and system consolidation and migration to the cloud.
- Trade Secret Protection – There are high costs to enterprises when data breaches result in unauthorized access to trade secrets. Zero Trust Data Security makes sure only the right people have access to the right data and reduces the threat of unauthorized disclosure due to insider or outsider threats.
- Automation – Enterprises can have more consistent enforcement of segregation of duties and internal control policies while cutting implementation and maintenance costs by automating business processes and internal controls.
NextLabs’ Zero Trust Data Centric Security
NextLabs’ Zero Trust Data Centric Security solutions implement Zero Trust and Data Centric security principles using dynamic authorization and Attribute-Based Access Control (ABAC), allowing organizations to determine the level of access to be granted based on attributes such as user identity, device type, location, and time of day. This provides organizations with a flexible and granular way of protecting and controlling access to sensitive data.
NextLabs’ solutions are designed to work seamlessly with existing security infrastructure and are compatible with a wide range of platforms and applications, including cloud-based services and legacy systems. This allows organizations to easily integrate NextLabs’ solutions into their existing security infrastructure and take advantage of Zero Trust principles without having to replace their existing systems.
Zero Trust Data Security Principles are incorporated into all NextLabs product lines, including:
- CloudAz, a unified policy platform that centralizes administration and utilizes the “never trust, always verify” principle, ensuring data is protected at any access point.
- Data Access Enforcer (DAE) helps enterprises protect data access from anywhere, by securing access and protecting critical data stored in databases and data lakes.
- SkyDRM ensures persistent protection of critical files and documents to protect data on the move and at rest.
- Application Enforcer which can be used to secure applications, enforce data security controls, and simplify role management.
For more information on NextLabs and Zero Trust, see our Technology page on Zero Trust Architecture (ZTA).





