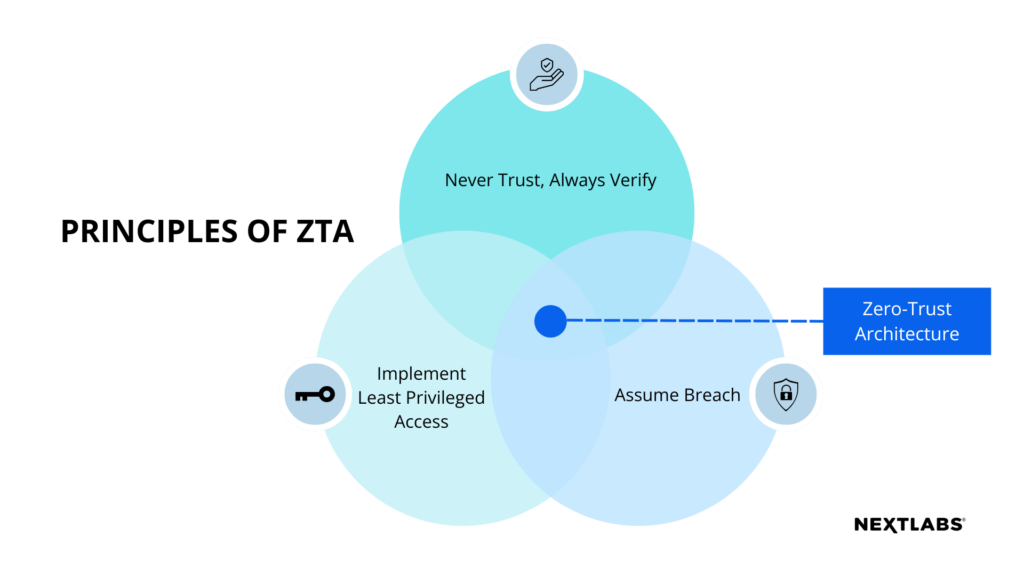
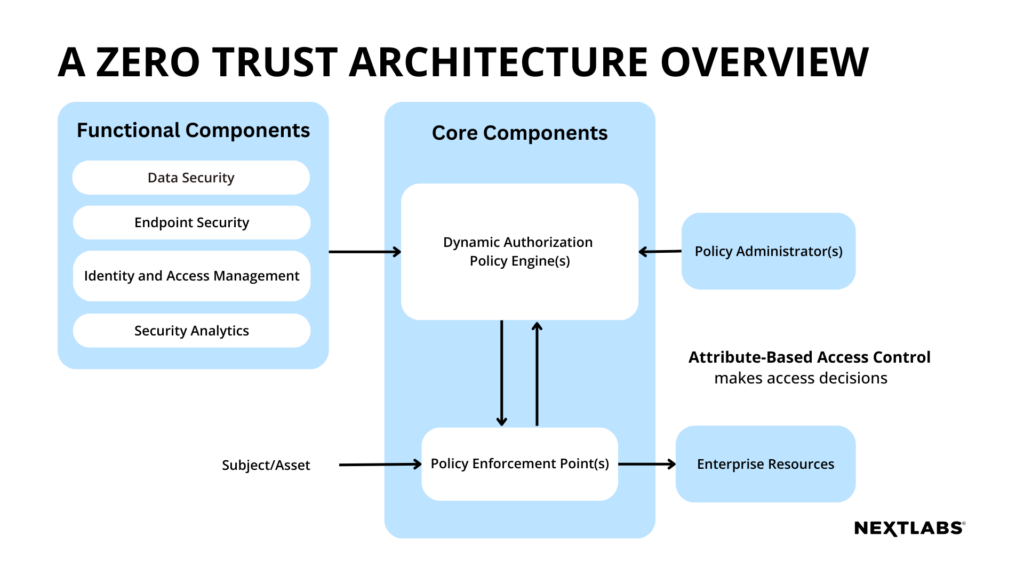
The technical components required of ZTA solution(s) include but are not limited to these main components: core, functional, and device and network infrastructure components, each responsible for a different aspect in the system.
The core components act as the brain to administer policies and manage authorization through the policy engine and policy administrator, and control subject access through the policy enforcement point (PEP). These components enable fine-grained access management and control in a simple and flexible way.
The functional components consist of different aspects of security management, and ensure data and resources are persistently protected in both internal and external environment. Specific measures include the data security component that protects data at rest and in transit, the endpoint security component that fights off external threats from managed or unmanaged devices, and identity & access management (IAM) component that manages subject accounts and identity records, along with the access to enterprise resources.
The device and network infrastructure components include devices that connect to the enterprise, and enterprise resources that store data and applications on premise, in the cloud, or at the edge. The core and functional components are integrated into the network infrastructure for successful implementation.

To comment on this post
Login to NextLabs Community
NextLabs seeks to provide helpful resources and easy to digest information on data-centric security related topics. To discuss and share insights on this resource with peers in the data security field, join the NextLabs community.
Don't have a NextLabs ID? Create an account.