In Part 1 of this series by Vinh Truong, CISSP, CEH, and Digital Transformation Advisor at KMV Group LLC, we learn how AI strengthens the ZTA framework by enhancing threat detection, adaptive access controls, and automating incident responses. Moving on to Part 2, we will explore the practical steps to integrate AI with the ZTA framework, including the steps needed to plan, tool selection, and implementation strategies. Additionally, we will look ahead to the future, discussing potential developments in AI and how organizations can prepare for the next phase of AI-driven cybersecurity. These insights will equip businesses with actionable guidance on enhancing their security frameworks while staying ahead of future challenges.
Organizations must quickly adapt as cybersecurity threats change rapidly. AI integration with ZTA will improve business information security measures. It can automatically detect anomalies, analyze a massive amount of data in seconds, adjust to dynamic threats in real time, and minimize potential risks.
This guide will help organizations better understand the advantages of integrating AI with the ZTA framework, the high-level implementation procedures, and potential pitfalls.
I. Steps to Integrate AI with Zero Trust
Incorporating AI with the ZTA framework has advantages, but doing so requires careful planning and execution so that the AI strengthens rather than weakens the security measures. Below are the essential steps of integration.
a. Assessment and Planning
Examining the company’s existing security landscape before implementing AI is essential. The project team needs to identify the areas that can benefit from the new system, and review the current information security policies, network topology, and access management standards. Important questions to think about are as follows:
- Which information security procedures are the best candidates for automation?
- What are the current risks that AI can help to mitigate?
- Where will the authoritative data source (such as network traffic, user behavior data, application logs, and SIEM) AI model have access to?
The next step is to work on the AI integration plan. It should include specific goals for using AI in information security and how it will improve the threat detection or incident response capabilities. Most importantly, it must align with the company’s goals and objectives.
b. Selecting and Implementation of AI Tools
When incorporating AI technologies into ZTA, the company must ensure that it selects technologies that meet its needs and can be implemented into its environment. The tool needs to address these areas, not be limited to them.
- AI-Driven Threat Intelligence: Using threat intelligence platforms built on AI can help speed up and improve the effectiveness of threat identification. These platforms use a variety of algorithms to analyze user behavior, traffic statistics, and intelligence feeds from external sources to predict and identify potential threats. The information security areas the tool can help monitor are devices, networks, data, applications, etc.
- Continuous User and Network Behavior Monitoring: The application of AI in security involves using tools to analyze user and network activity in search of anomalies that may be signs of an attack. This is useful in the event of unanticipated risks arising in the future, and it minimizes the impact of the attacks. AI systems may monitor potential threat patterns, such as insider threats or other compromised accounts within a company and take action to stop the threats.
The collaboration of all stakeholders needs to be engaged from the project’s inception. The implementation needs to be in phases: testing, pilot, one workload at a time, etc., and it is also critical that all stakeholders, like applications owners, IT team, Security team, data scientists, etc., sign off on the user accepting test plan.
c. Policy and Access Management
Micro-segmentation and least privileged access control are the cornerstones of ZTA.
- AI-Enhanced Access Control Policies: AI can enhance access control policies in real time to adapt to the evolving threat landscape. For example, AI can analyze user access requests based on the user’s behavioral patterns, time of day, device location, and internal or external.
- Identity Verification and Authentication: AI can improve the existing identity identification and authentication processes. For example, facial recognition and behavioral biometrics can be used with AI to improve identification accuracy and combined with other factors to enhance the authentication process.
d. Continuous Monitoring and Improvement
AI integration with ZTA does require continuous monitoring and improvement. To stay effective, it must be reviewed and improved as threats change.
- Continuous Threat Monitoring: AI provides real-time security monitoring for an organization’s environment. As threats evolve, new threat data needs to be used to train the AI model. An AI-based system can also perform real-time vulnerability scanning and apply remediation where appropriate.
- Model Updating and Fine-Tuning: As a result, the AI model must be updated with new information and potential threats as needed, and it must be incorporated into company’s information security policies and procedures.
These are some of the benefits of integrating AI with ZTA. These features allow the company to stay ahead of new threats and keep the data safe.
II. Future Prospects and Developments
Several new technological developments and emerging trends are about to completely change the cybersecurity environment as AI and ZTA Framework continue to develop. Future advancements in this area are expected to improve the capabilities of AI and Zero Trust, giving enterprises access to more advanced defenses against a constantly evolving threat landscape.
Emerging AI Technologies and Their Potential Impact on Zero Trust
Many innovative AI technologies are becoming popular and have the potential to improve Zero Trust systems even more. These technologies can make security measures more accurate, flexible, and effective:
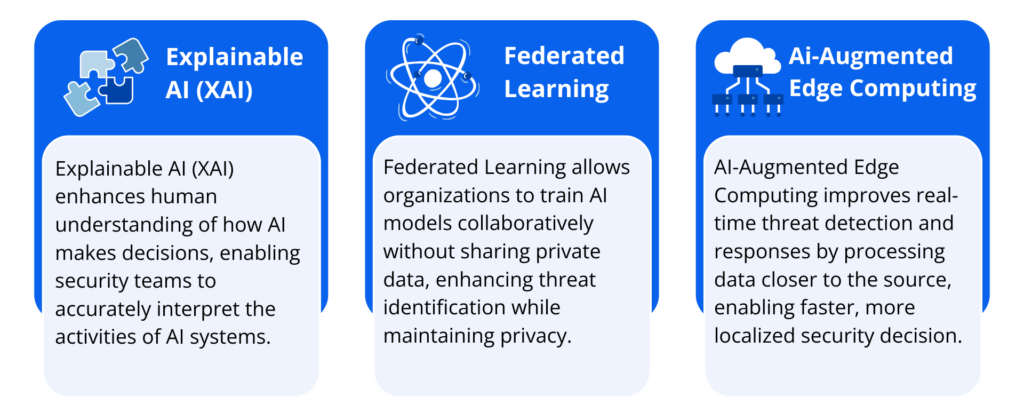
- Explainable AI (XAI): Transparency in the decision-making process of AI systems is becoming increasingly important as they play a more significant role in cybersecurity. The goal of explainable AI is to improve human comprehension of AI decision-making processes so that security teams can more confidently and accurately interpret the activities of AI systems.
- Federated Learning: Multiple organizations can jointly train AI models without exchanging private information. Federated learning can improve ZTA by allowing enterprises to share their threat intelligence while protecting the privacy of their data. This strategy may produce more efficient threat identification and incident response across industries.
- AI-Augmented Edge Computing: AI can be implemented at the edge of networks to improve real-time threat detection and response. Edge computing, which processes data closer to the source (like IoT devices), is becoming more popular. AI-augmented edge computing can decrease the time it takes to identify and neutralize threats in distributed systems, providing quicker, more localized security decisions.
III. Preparing for the Future of AI and Zero Trust
Organizations need to be ready as new trends and technology continue to influence AI and ZTA framework in the future. They need to be knowledgeable and flexible. This entails allocating appropriate budgets for AI tools, providing cybersecurity personnel with training, and keeping up with changes in data protection regulations, AI ethics, and industry best practices.
AI and the ZTA framework will continue to develop, providing businesses with the means to keep up with and combat cybercriminals.
To comment on this post
Login to NextLabs Community
NextLabs seeks to provide helpful resources and easy to digest information on data-centric security related topics. To discuss and share insights on this resource with peers in the data security field, join the NextLabs community.
Don't have a NextLabs ID? Create an account.