Enterprise Digital Rights Management (E-DRM), sometimes referred to as Information Rights Management (IRM), is the common term for digital rights management (DRM) technologies that cater to enterprise use cases, many of which involve protecting sensitive information from unauthorized access and use.
What is DRM?
Traditional Digital Rights Management (DRM) technologies are usually associated with preventing the unauthorized access and distribution of consumer-facing media such as games, music, and movie. For example, locking specific programs so that they cannot be accessed in certain regions/countries, another example would be licensing control when a piece of media is tied to an account, and you must be logged in to access said content.
While this may be secure enough for consumer-facing software and content, there are many workarounds that many consumers have found. While this is a concern for businesses, it will not cause a large-scale loss. However, this is not the case for business-critical data and files, while these must also be distributed and shared with multiple collaborators including employees, partners, and customers; a data leak or wrongful disclosure could lead to significant impact and loss to the business.
Enterprises need DRM technologies that match the security needed to ensure their files are safe without sacrificing the ability to efficiently collaborate, share, and edit.
Enterprise Digital Rights Management (E-DRM)
The E-DRM model addresses the data protection needs of the enterprise to collaborate and share business data across internal and external stakeholders. E-DRM technology allows for sensitive enterprise information and data to be created, viewed, modified, and distributed securely. It protects sensitive enterprise information from unauthorized access, use, and distribution by applying rules to the information distributed in electronic documents.
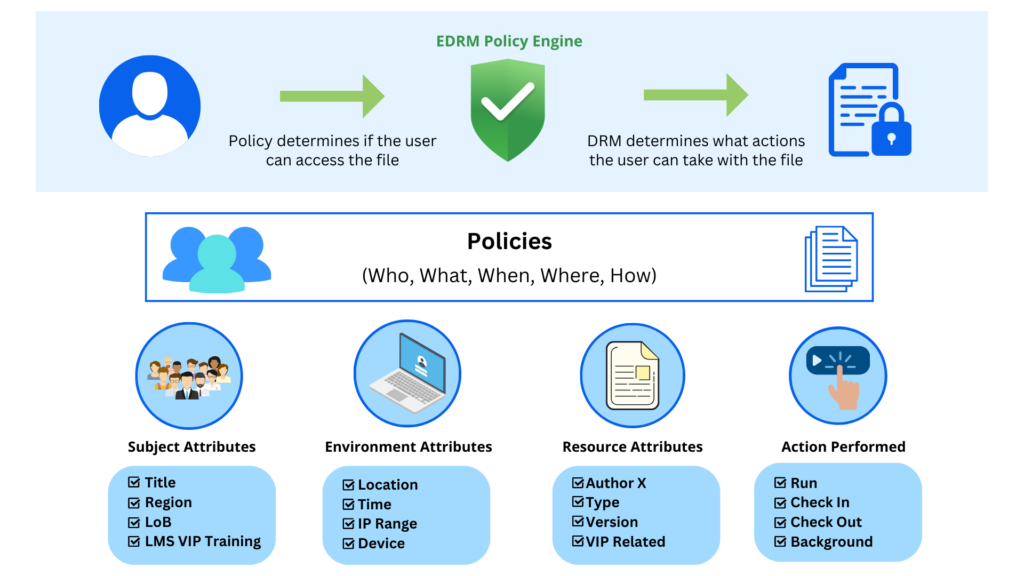
E-DRM policies determine dynamically based on the identity of the recipient(s), what permission and user action is granted to control recipients from specific use activities like viewing, modifying, printing, forwarding, making a copy, extracting content, and expiration. Policies can be updated or revoked even after a document has been distributed.
Enterprise Digital Rights Management solutions are frequently used to reduce exposure to information risks and prevent data loss when communicating and collaborating with partners. E-DRM protects information against theft, misuse, or inadvertent disclosure, and mitigates the business, legal, and regulatory risks of collaboration and information exchanges with partners, customers, and across the extended enterprise.
Different Use Cases for Different Data
Before discussing some more specific Enterprise Digital Rights Management deployment situations, the simplest aspect of any use case is the actual data, its format, and its accessibility. E-DRM utilizes the power and flexibility of a dynamic authorization policy engine with fine-grain access & usage controls and attribute-driven policy to protect, track, and monitor data as they are being shared and consumed. These policies, which are written to apply to certain attributes (e.g. location, role, device, type of data, etc.) to apply appropriate protection and usage controls on data varying in value and safeguarding requirement. These assets and use cases usually fall into two broad generalizations:
- Highly classified mission-critical files, including engineering plans, product recipes, financial data, and so forth. Protecting these files using a highly secure, centrally managed, and monitored solution is a necessity.
- User-created arbitrary files, such as emails, datasheets, or authored documents. While the impact of these files being leaked may not match mission-critical documents, they are much more common and in turn vulnerable. Protecting these files requires an easy to use highly scalable solution that can be implemented to many files without a large amount of IT overhead.

Using E-DRM to balance “Need to Share” with “Need to Protect”
Across industries, companies are required to share and make information available to the global workforce and business partners. Sharing business-critical information is essential in conducting business, however, it is no longer possible to contain them within the network perimeter. An increasing amount of data is residing in the cloud, on mobile devices, and being shared with business partners, while business stakeholders are expecting easier and faster access to data anytime and anywhere.
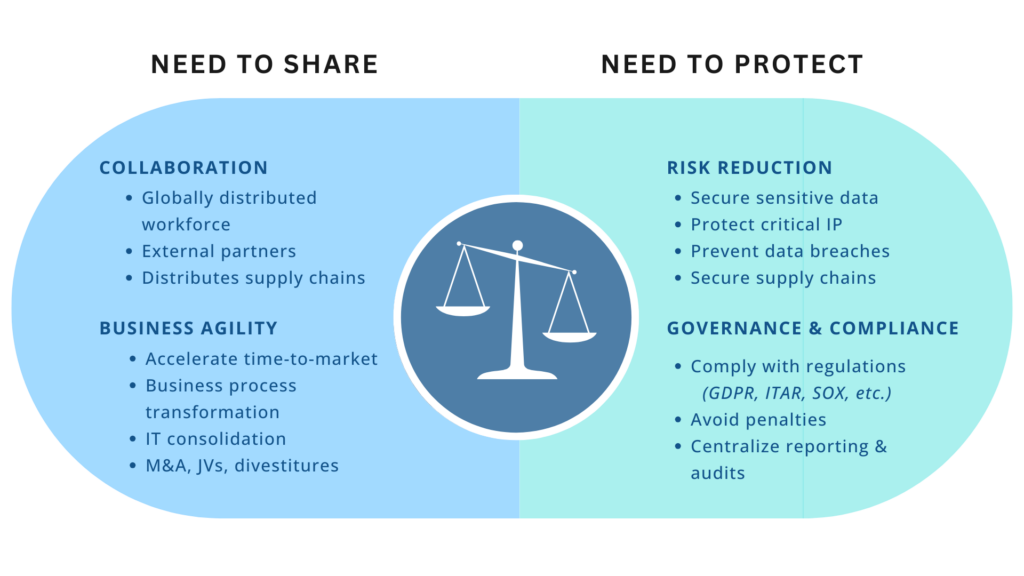
In today’s digital economy, organizations need to collaborate with supply chain partners, outsourced partners, and many others business partners and customers. In order to work effectively and efficiently, organizations need to be able to share their most sensitive assets with proper safeguards.
How can organizations safeguard information sharing to protect their crown jewel, trade secret, and sensitive data while being able to share freely? Below are examples of how Enterprise Digital Rights Management technology can be used to protect critical data:
- Automate protection of content shared and downloaded from cloud collaboration platforms (such as SharePoint) or exported from a business application. Using centrally managed policies, data can be safeguarded and tracked persistently at the individual file level. This method not only provides a flexible way to safeguard access to files of varying importance but is also fairly straightforward requiring no changes in workflow.
- Provide an easy-to-use tool for business users to protect content on the end user’s device. This allows users to write and create policies for files, dictating the use of files on their client’s devices. These policies can control access, sharing, and editing rights seamlessly and transparently within the application such as word processors, CAD tools, and ERP applications.
- Secure data in the cloud – E-DRM provides an effective approach to allow organizations to control access, sharing, and editing of their files stored in the cloud without sacrificing mobility and collaboration.
Monitoring and Tracking Data
While DRM architecture is heavily associated with the security and protection of files, one of the other benefits it has for enterprise use cases is the ability to monitor data usage. The use of Central Policy management allows organizations to keep tabs on their files, keeping logs of every time a user attempts to access, edit, or share a file. This level of control helps to keep a tight grip on the life cycle of documents and files. For example, E-DRM solutions may be used to enforce the deletion of files, data, and assets in the case of a partnership ending, ensuring that there is no data breach. This can also be used internally to make sure that employees are always working with the most up-to-date information and assets. This allows for greater protection when collaborating with partners, and helps to reduce the risk of data leakage.
Do I Need E-DRM?
While Enterprise Digital Rights Management technology protects files that every organization works with, it is not necessary for every business. E-DRM architecture greatly benefits enterprises that rely on electronic documents not just as the means to share and disseminate information but also to collaborate, whether it be with partners or clients. In an increasingly digital work environment, many international organizations need to collaborate with partners outside their organization, however, this leaves them vulnerable to data leakage.
Whoever a business shares data with it is critical to limit the distribution and use of certain classes of documents to certain groups of users inside and outside the enterprise. One of the primary advantages of electronic documents and data is their ease of movement, but depending on who it moves to this can have a negative effect. Traditional file-sharing systems may work for non-critical files, but it is not worth risking mission-critical documents and data. Data leakage can come from multiple sources, both internal and external, and human error can mean that your files end up in front of the wrong people.
The Enterprise Digital Rights Management system presents a method to send and share data with external users while simultaneously ensuring that that same data does not fall into the wrong hands. It is a digital access control solution that can combat data leakage by going a step beyond encryption, allowing for a robust fine-grain access control method without sacrificing the ability to share and collaborate.
If your enterprise collaborates with external partners, you may worry about how to safeguard the files and documents you are sharing. While partnerships are built on mutual trust and business agreement, data breaches often happen as the result of human error. Enterprise Digital Rights Management technology allows organizations to automate the protection of files and data shared with centrally managed policies. New policies can be added quickly as new business requirement merges or when condition changes to ensure the right users access to the right data. E-DRM provides the ability to control, track, and revoke access with the facility to audit and report user access.
Watch our “What is EDRM?” video for a deeper dive into the subject of enterprise digital rights management.






