With microservices, only the service needed for the task will be activated. This reduces the need for the whole IT infrastructure to be deployed all the time, thus reducing the complications and cost of growth. In addition, more resources can be allocated to innovation as it enable teams to develop and test services in the application without affecting the other services. This allows organizations to manage and scale the applications easily, which helps companies easily modernize their IT infrastructure.
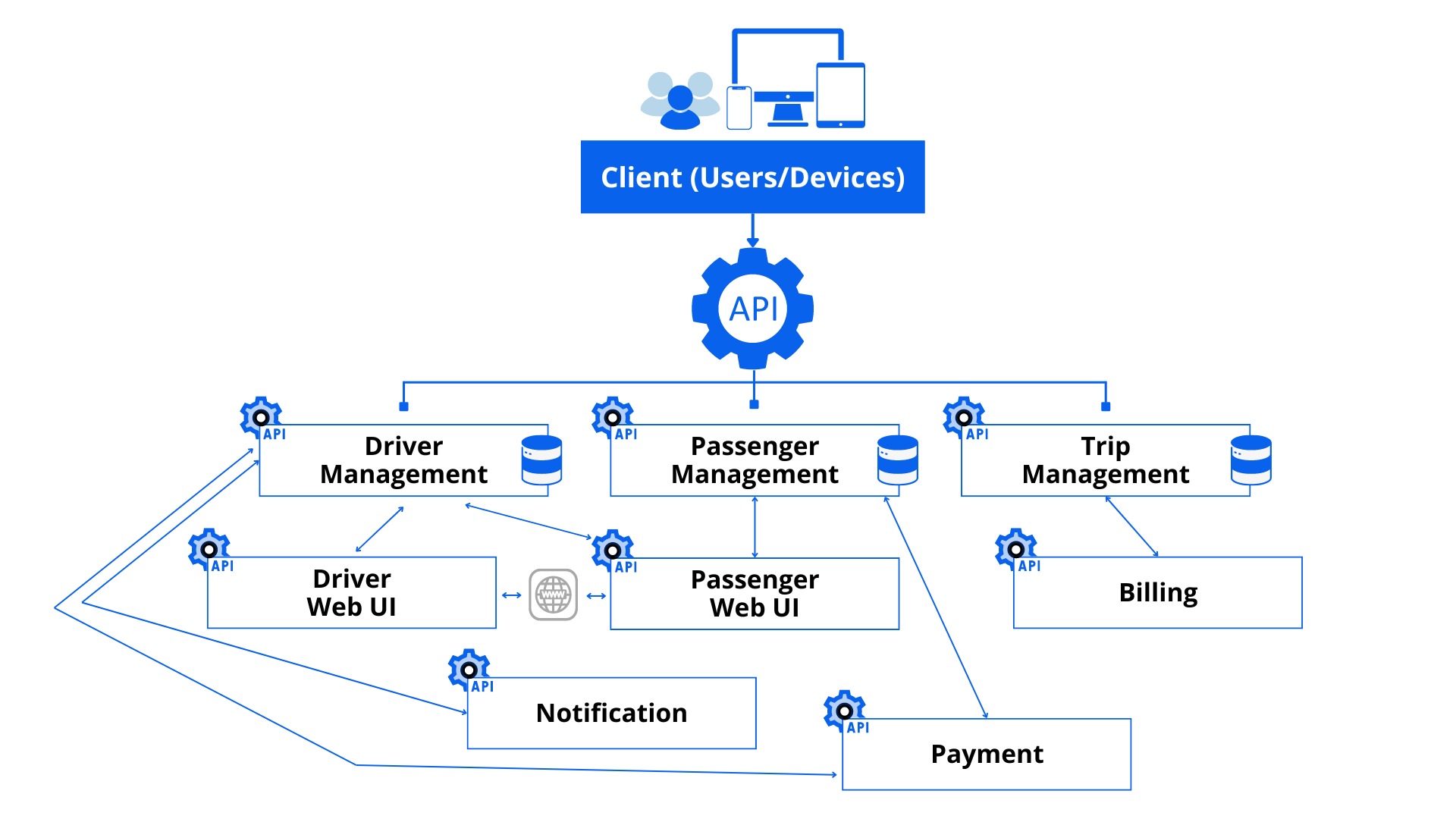
Companies like Uber have adopted this kind of architecture to overcome the challenges of a monolithic architecture. Uber’s platform had encountered challenges and complexity to efficiently make modifications, fix bugs and scale with the monolithic architecture. To overcome this, Uber had moved to a microservices architecture where they built individual microservices for services such as driver management, passenger management and trip management.

To comment on this post
Login to NextLabs Community
NextLabs seeks to provide helpful resources and easy to digest information on data-centric security related topics. To discuss and share insights on this resource with peers in the data security field, join the NextLabs community.
Don't have a NextLabs ID? Create an account.