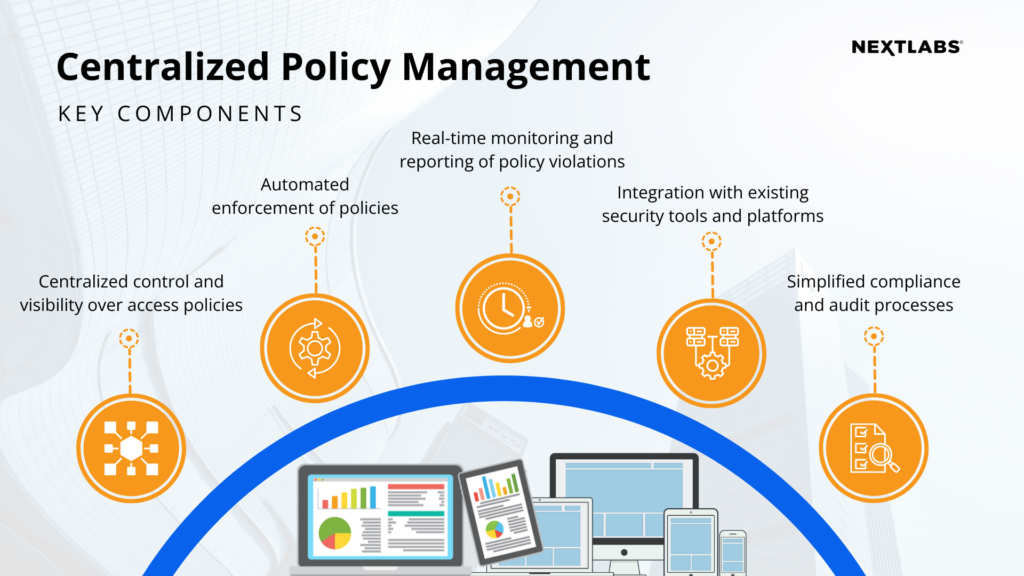
As businesses expand into new regions and markets and adopt digital technologies, they face an increasing number of security challenges. To overcome this, many organizations are turning to centralize policy management with Zero Trust security model, which assumes that all devices, users, and networks are untrusted until proven otherwise.
Centralized policy management is an essential component of a successful Zero Trust implementation. By consolidating and managing access policies from a central location, a centralized policy management system helps organizations streamline their security posture, automate policy enforcement, and ensure compliance with regulations and best practices.

To comment on this post
Login to NextLabs Community
NextLabs seeks to provide helpful resources and easy to digest information on data-centric security related topics. To discuss and share insights on this resource with peers in the data security field, join the NextLabs community.
Don't have a NextLabs ID? Create an account.