Zero Trust Policy Management (ZTPM) is an essential component of Zero Trust architecture, which has gained popularity in recent years as a security model that trusts no user or device by default. With the proliferation of data breaches and cyber attacks, organizations are seeking to adopt a Zero Trust approach to secure their sensitive data and critical assets. However, implementing Zero Trust is not a one-time process, but a continuous journey that requires effective policy management. In this blog post, we will discuss the importance of ZTPM and how it is crucial to take a data-centric approach to achieve effective Zero Trust policy management.
In a Zero Trust environment, security policies should be based on the principle of least privilege, where users and devices are only granted access to the resources they need to perform their duties. ZTPM involves defining and enforcing policies that ensure access to sensitive data and critical systems is only granted to authorized users and devices. ZTPM includes the creation, enforcement, and continuous monitoring of access policies, as well as the management of identity and access management (IAM) systems. Effective ZTPM helps organizations to prevent unauthorized access, detect potential security incidents, and respond quickly to security events.
Ensuring appropriate access for employees has become an increasingly difficult challenge and is now seen as one of the largest issues in technology audits, insider threat and cyber risk prevention, and compliance adherence. Previously authorization was handled manually by administrators, however, this isn’t efficient and is error prone.
This creates a need for runtime authorization, where authorization decisions are made in real-time when the user is accessing an application or data. By evaluating the decision at runtime, when an increased amount of information about the user and their actions is available, it allows more fine-grained decisions to be made. Because of this, runtime authorization has become a focal point for developing the next generation of identity-centric access controls. This includes both human and non-human use cases, which can support the high volume and velocity of access to modern apps, computing units, data objects, and underlying networks.
Runtime authorization systems require an architectural view of the end-to-end access path. This path spans from the authenticated subject of the target object, considering all tiers, intended actions and computing environment requirements. Each authorization control in this path requires a set of policy management capabilities to define and maintain what policies should be enforced, while also supporting runtime services to evaluate and enforce the policies in real time.
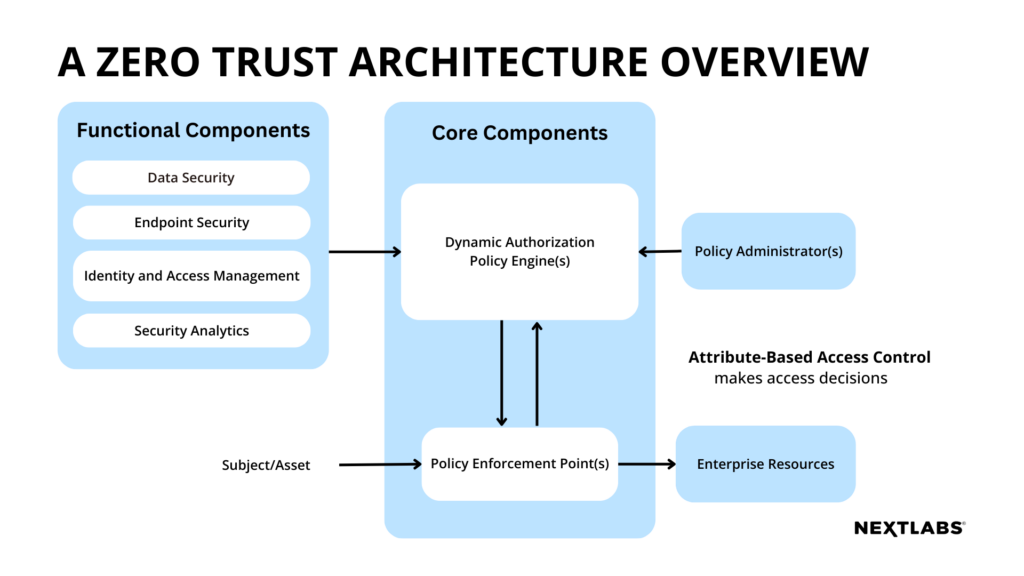
Taking a data-centric approach to ZTPM is essential for effective Zero Trust policy management. Data-centric security (DCS) is a security model that prioritizes the protection of data, regardless of its location or how it is accessed. In a data-centric security (DCS) model, data is secured using encryption, access controls, and other security measures to ensure that it remains protected throughout its lifecycle. By focusing on the data, rather than the user or device, data-centric security (DCS) provides a more comprehensive approach to security that can be applied across all environments, including cloud, on-premises, and hybrid environments.
Effective ZTPM requires a comprehensive understanding of an organization’s data assets, including where the data is located, who has access to it, and how it is being used. A data-centric approach to ZTPM involves creating policies that are focused on the protection of data, rather than the user or device. These policies include the use of encryption, access controls, and data loss prevention (DLP) technologies. By encrypting data at rest and in transit, organizations can ensure that their data remains protected, even if it is accessed by an unauthorized user or device. Access controls, such as multi-factor authentication (MFA) and attribute-based access controls (ABAC), can ensure that only authorized users have access to sensitive data.
Another key aspect of ZTPM is the continuous monitoring and enforcement of policies. In a Zero Trust environment, policies should be constantly monitored to ensure they are being enforced and remain effective. By monitoring user and device behavior, organizations can quickly detect potential security incidents and respond before they escalate into a full-scale security breach. A data-centric approach to ZTPM includes the use of analytics and machine learning to identify patterns of behavior that may indicate a security threat.
In conclusion, effective Zero Trust policy management is essential for organizations seeking to secure their sensitive data and critical assets. Taking a data-centric approach to ZTPM involves focusing on the protection of data, rather than the user or device. By creating policies that prioritize the protection of data, encrypting data at rest and in transit, and continuously monitoring and enforcing policies, organizations can achieve effective Zero Trust policy management. As cyber threats continue to evolve, adopting a Zero Trust approach to security and implementing effective ZTPM is becoming increasingly important for organizations of all sizes and industries.
To comment on this post
Login to NextLabs Community
NextLabs seeks to provide helpful resources and easy to digest information on data-centric security related topics. To discuss and share insights on this resource with peers in the data security field, join the NextLabs community.
Don't have a NextLabs ID? Create an account.