Home | Innovations | Technology
Technology
Never stop evolving – we’re always in pursuit of the next ground breaking technology
Home | Innovations | Technology
Never stop evolving – we’re always in pursuit of the next ground breaking technology
At NextLabs, our mission is to protect data anywhere and anytime. We work relentlessly to develop technologies that empower enterprises to confidently tackle today’s data security challenges.
We created groundbreaking patents and technologies in Zero Trust policy enforcement and Data-Centric Security (DCS). NextLabs has attained a portfolio of 90+ approved and 30+ pending patents based on the advanced technologies we have developed in dynamic authorization, Policy and Attribute-Based Access Control (ABAC), real time policy enforcement, 4GL policy language, high performance policy optimization, and next-generation digital rights management (E-DRM).
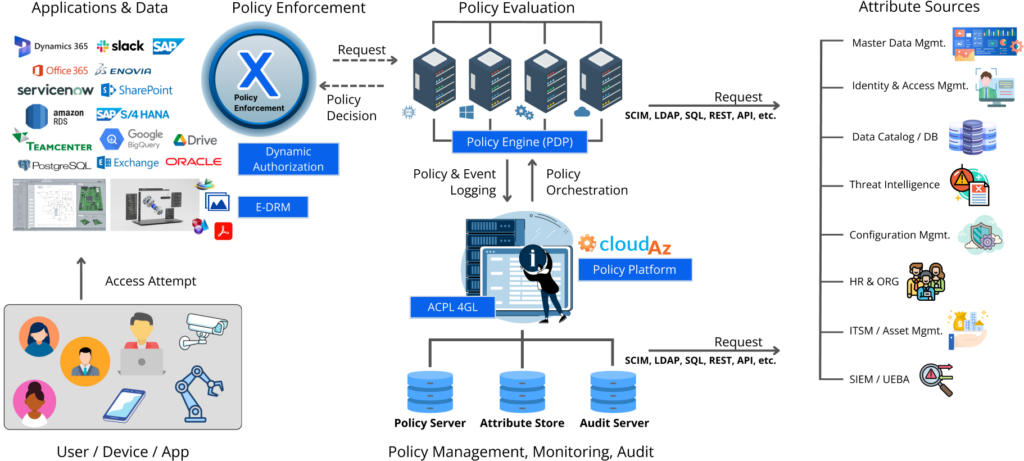
As a result of NextLabs’ technologies, the solutions provided work seamlessly with enterprise IT and vast cloud infrastructures. When a user, device, or application attempts to access an application or data, the policy engine (PDP) enforces the policy written by administrators through the use of dynamic authorization, policy-based access control (PBAC), and enterprise digital rights management (E-DRM).
At the heart of the NextLabs portfolio is our patented dynamic authorization and policy-based access control technology based on the zero trust policy engine. Dynamic authorization is a technology in which authorization and access rights to an organization’s network, applications, data, or other sensitive assets are granted dynamically in real-time using attribute-based rules and policies. The policies are supported by ACPL, a fourth-generation non-procedural language that allows users to create business-level policies in plain English, making it more accessible and easier to understand for those who may not have a technical background.
NextLabs’ products use a Zero Trust data-centric approach to dynamically enforce data security policies, protecting data whether it is at rest, in use, or on the move. Data is protected within applications as well as in structured and unstructured data stores by NextLabs’ dynamic authorization and real-time policy enforcement technology, allowing data access policies to be enforced at the time of access, wherever the data is being accessed. NextLabs’ policy engine uses policy-based access control and the principle of least privilege to evaluate and authorize access in real-time, based on user, device, resource, and contextual attributes at every access attempt.
The policy enforced is managed in the CloudAz zero trust policy platform, which provides a centralized system for administrators to author policies easily using the Policy Studio, a graphical editor for ACPL. The policy platform allows organizations to efficiently manage and enforce security rules across data, applications, and documents, while also monitoring, tracking, and reporting any risky access activities.
Attributes from a variety of sources can be used with the zero trust policy platform to author policies. When an access attempt is made, the attributes of the user, device, or application are validated against the policy; if the attributes are aligned with the policy, the access attempt is granted. If the attributes are not aligned with the policy, the policy engine will deny access.
A non-procedural language that utilizes a natural language syntax like English designed to define context-aware security policies across applications and systems based on attribute-based access control (ABAC) principles. It is the underlying policy language of NextLabs CloudAz policy platform.
A software component built on a distributed architecture optimized to deliver high performance and highly scalable real-time and context-aware authorization decisions across application and data sources based on attribute-based policy.
The leading native zero trust multi-tenant policy platform with rapid policy development, robust governance, policy orchestration, and analytics functionality for managing authorization policies and provide continuous monitoring of data access activities across applications and services.
A multi-layered and policy-driven approach that focuses on safeguarding data itself by applying a variety of data security controls such as attribute-based access control, data obfuscation, data segregation, digital rights management (DRM), and data loss prevention directly to data in real-time.
The first Enterprise Digital Rights Management technology built-on Zero Trust Architecture to control access, secure sharing across enterprises, and protect usage of file and unstructured data of any types with security that stays with the file wherever it lives or travels to.
A technology framework that allow organizations to seamlessly apply security and compliance controls to existing applications without additional integration effort or customization, enabling rapid implementation of zero trust security model.
As government agencies integrate data to power AI initiatives, the risk of exposure grows dramatically. Traditional perimeter defenses are no …
Learn what data scrambling is, how it works, and why it’s essential for protecting sensitive information in testing, development, analytics, …
Expanding collaboration across project teams, suppliers, and international partners significantly increases the number of touchpoints where sensitive SAP data can …
In today’s digital-first world, the old ways of defending enterprise systems—guarding the network perimeter and trusting everything inside it—just don’t …
In research, design, and engineering environments, product data sits at the heart of innovation. It contains intellectual property, technical specifications, …
Discover how Data-Centric Security enables Zero Trust Application Protection, securing enterprise apps, workloads, and APIs against modern threats.