A Policy Enforcement Point (PEP) protects an enterprise’s data by enforcing access control as a vital component of the attribute-based access control (ABAC) architecture. ABAC, also known as policy-based access control for IAM, defines an access control paradigm whereby a subject’s authorization to perform a set of operations is determined by evaluating attributes associated with the subject, object, requested operations, and, in some cases, environment attributes.
ABAC comes with a recommended architecture which is as follows:
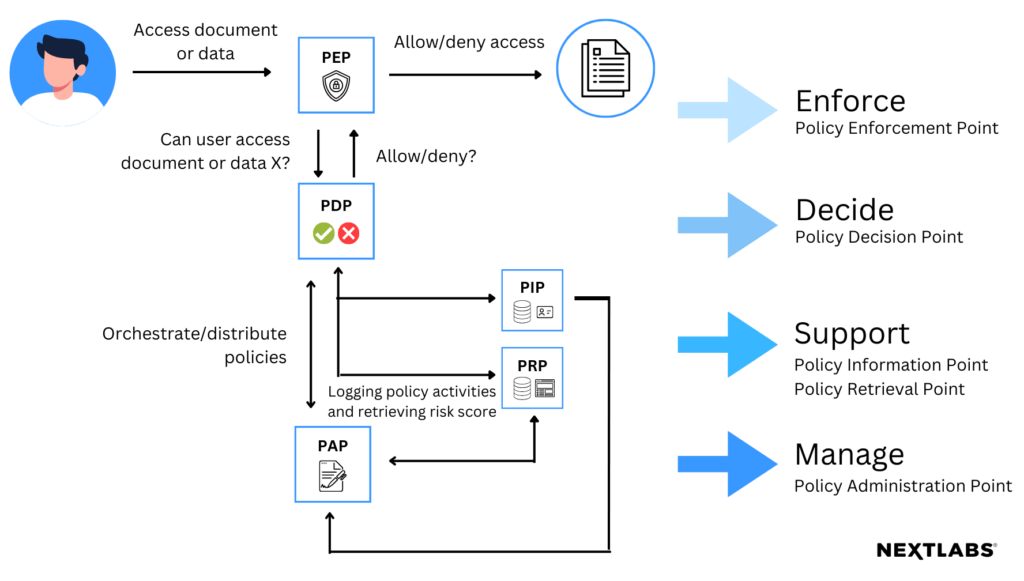
- The PEP or Policy Enforcement Point: it is responsible for protecting the apps & data you want to apply ABAC to. The PEP inspects the request and generates an authorization request from which it sends to the PDP.
- The PDP or Policy Decision Point is the brain of the architecture. This is the piece which evaluates incoming requests against policies it has been configured with. The PDP returns a Permit/ Deny decision. The PDP may also use PIPs to retrieve missing metadata.
- The PIP or Policy Information Point bridges the PDP to external sources of attributes e.g. LDAP or databases.
- The PAP or Policy Administration Point: feeds policy to the PDP. It provides a centralize depository to manage policy especially for the enterprise architecture.
How Does a Policy Enforcement Point Work?
Let’s walk through how a PEP works in the ABAC architecture. First, a user takes action on a resource by making a request to the gate which protects that resource, which is a Policy Enforcement Point (PEP). The PEP will then form a request based on the user’s attributes, the resource they wish to access, the action they are attempting to take on that resource, and other relevant information pertaining to the request. The PEP sends this request to the PDP, which evaluates the request and the policy that applies to the request and decides whether access should be granted. That answer is then sent back to the PEP, which can then allow or deny access to the requester.
Why are PEPs Necessary?
A PEP is responsible for receiving authorization requests from the PDP for evaluation. The PDP and PEP work together to interpret policies to control the behavior of the network devices in order to satisfy both the users and administrators of network resources. However, a PEP is only responsible for requesting and evaluating an authorization decision and doesn’t require any authorization logic. Unlike PDPs, PEPs cannot be centralized in a SaaS application. This is because authorization and access control are required to be implemented throughout an application and its access points. PEPs can be applied to APIs, microservices, or any point in the application where access control is needed. Making PEPs pervasive in an application ensures that authorization is verified often and independently at multiple points.
To learn more about the other components of the ABAC architecture, read our previous blogs on PDP, PAP, and PIP.
To comment on this post
Login to NextLabs Community
NextLabs seeks to provide helpful resources and easy to digest information on data-centric security related topics. To discuss and share insights on this resource with peers in the data security field, join the NextLabs community.
Don't have a NextLabs ID? Create an account.