Persistent File Protection: Explained
In today’s dynamic digital landscape, it is crucial to secure assets, whether it be inside or outside the organization. Chasing dynamic data with static security models will not support a fast-moving company. As more data is shared across enterprise networks, file servers, and cloud environments, organizations need a solution to not only protect data within the enterprise but also when shared. This brings about the question, how do you continuously protect data once the file has been shared?
Enter persistent protection—persistent file protection ensures sensitive documents are protected regardless of where the document travels and who it is shared with. Oftentimes, this is achieved through Digital Rights Management (DRM) technologies, which are used to manage, control, and secure data. When introducing persistent file protection to an enterprise, the objective is to protect business-critical data from unauthorized access, use, and distribution. To achieve this, policies in the enterprise’s system can be written to selectively prevent file recipients from completing specific activities, such as copying, printing, forwarding, or cut and paste.
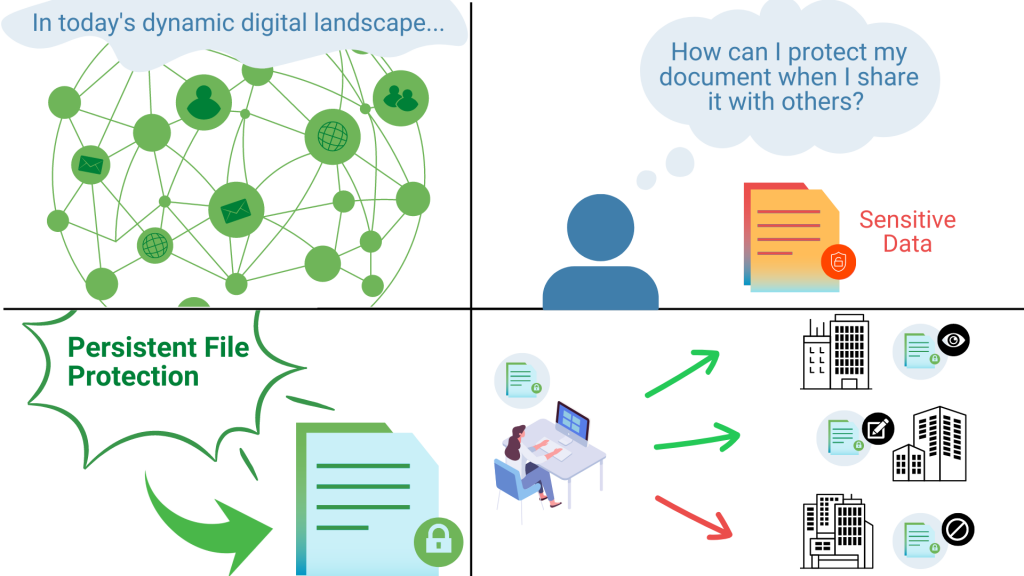
This allows enterprises to balance their need to share and protect information, increasing efficiency when sharing data. Through this, data is persistently protected when being shared across supply chains, global business units, and partners.
Why Do You Need Persistent File Protection?
Persistent file protection provides the stability required in our volatile digital environment, where business-critical data can be easily reproduced in numerous copies and shared without knowledge. If not overseen with caution, the spread and transmission of data can quickly spiral out of control, taking unpredictable routes into untrusted environments.
Traditional security models, which prioritize protecting the network perimeter, place responsibility in the hands of users to secure and monitor their data, facing higher risks of unauthorized access and distribution of sensitive data. In contrast, persistent file protection applied with data-centric security in mind, alleviates the burden from users and enforces security within the unstructured data itself, diminishing security risks in collaborative, dynamic environments.
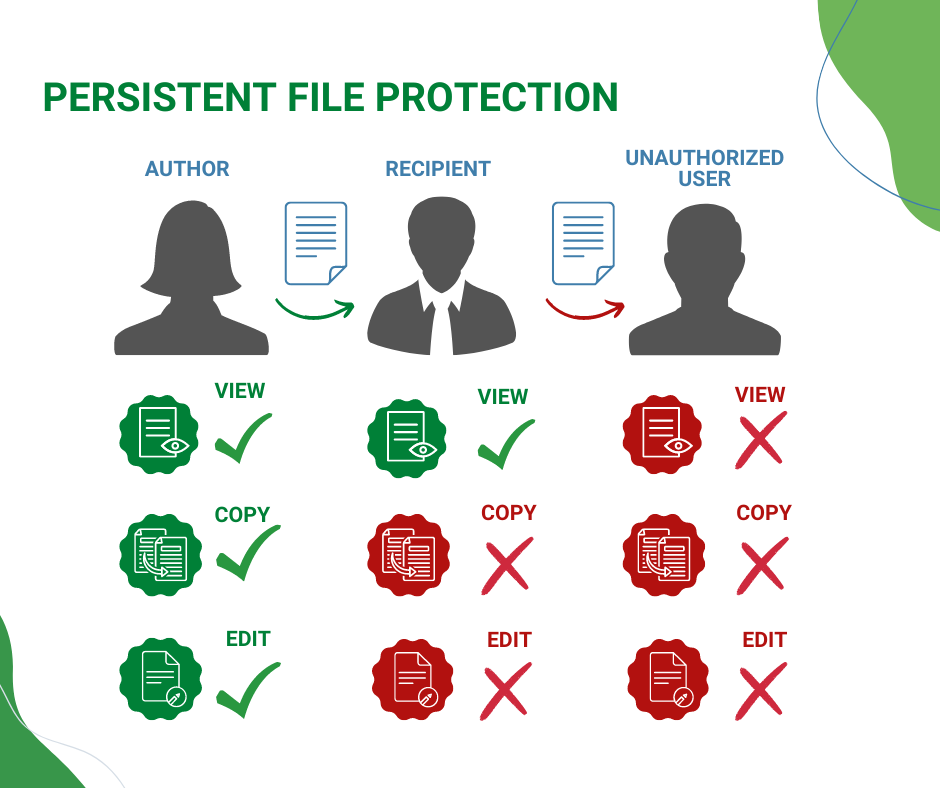
Written policies enable authors to ensure consistent and persistent protection across the data’s lifecycle, regardless of where it is stored or who it is handled by. By ensuring only authorized users have access, persistent file protection helps to mitigate business, legal, and regulatory risks of collaboration and information exchanges within the organization, with partners, and customers.
When persistent file protection is combined with a system that can track and monitor shared data, it increases the security of business-critical information. This allows administrators to understand when unauthorized access attempts are made, while protecting against theft, misuse, or inadvertent disclosure. For example, the water mark generated with user ID, date and timestamp, allows organizations to smoothly trace back cases of fraudulent users and attempted leaks.


To comment on this post
Login to NextLabs Community
NextLabs seeks to provide helpful resources and easy to digest information on data-centric security related topics. To discuss and share insights on this resource with peers in the data security field, join the NextLabs community.