Zero Trust Architecture: Explained
A traditional security model implicitly trusts everything inside an organization’s network, leaving plenty of loopholes for human error and insider threats. This is no longer sufficient under today’s circumstances: many are now working remotely, with enterprise teams spreading across a variety of countries and companies shifting to complex hybrid cloud systems. Given these challenges, it is becoming increasingly difficult to define network perimeters. Additionally, when subjects (end users, applications, non-person entities requesting information) are given broad access to resources within the network perimeter, the compromise of a single subject can snowball into massive data breaches.
As defined by NIST, a zero-trust architecture (ZTA) employs a data-centric methodology that focuses on protecting resources over the network perimeter. Since the network perimeter is no longer the key component to safeguarding enterprise data, a zero-trust strategy shifts its line of sight to identifying and authenticating users and devices. Zero-trust encompasses a set of principles that safeguards subjects, enterprise assets, and resources. These principles include “never trust, always verify”, “assume breach” and “least privileged access”.
ZTA, with its “never trust, always verify” principle, holds no implicit trust when it comes to subjects within the network perimeter. This allows it to enforce more granular levels of security control. When every stage of a digital transaction is evaluated for authorization, users are less likely to overstep the boundaries of what they are allowed to access.
By assuming that a data breach has already happened, ZTA prepares for worst case scenarios and protects sensitive data accordingly when attacks do occur. This goes hand in hand with its principle of enforcing “least privileged access”, where users and applications are granted the least amount of access needed to complete their duties effectively.
Why Zero Trust Architecture?
Combined with dynamic automated controls, ZTA allows enterprises to easily reach regulatory compliance, achieving a balance of security, availability, usability, and cost efficiency.
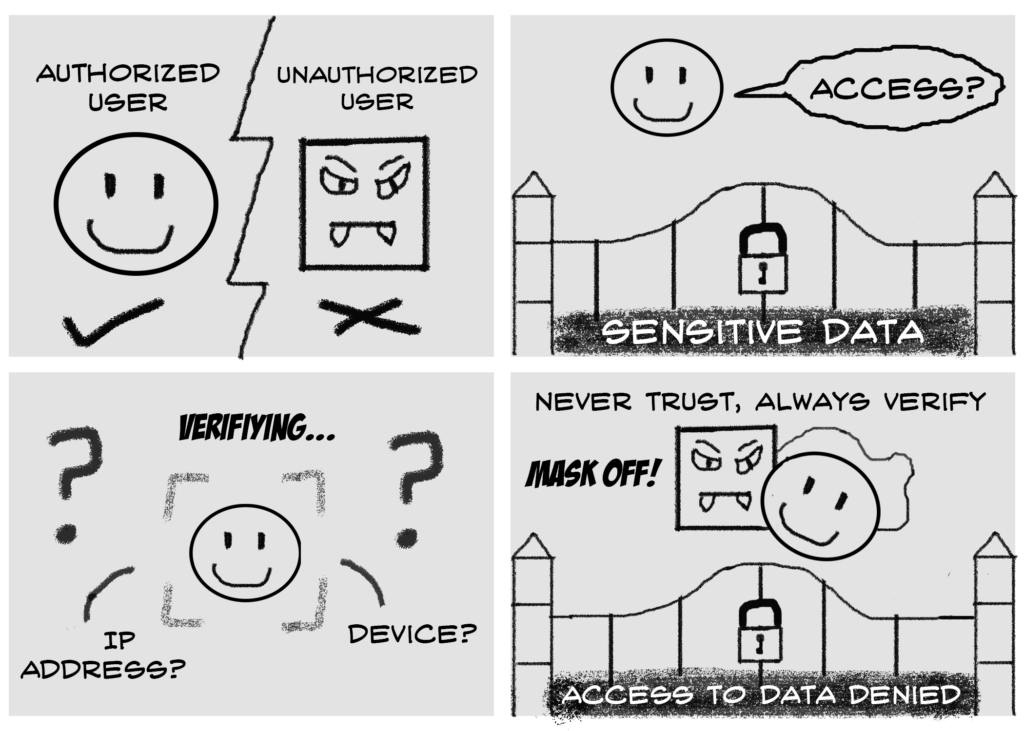
Especially in an environment full of collaborative information sharing, ZTA’s enforcement of “least privileged access” helps to safeguard business-critical information from unauthorized access. With real-time access control, users are reliably verified and authenticated before each session.
ZTA also allows organizations to better track and monitor patterns in user behavior. With increased visibility over resources, enterprises can detect suspicious activity and protect data accordingly. Due to the absence of a “trusted” network and location, every connection is subjected to verification, reducing the overall risk of malicious attacks. When security events do happen, the simplified security architecture of ZTA allows enterprises to respond swiftly and effectively.
To learn more about ZTA and its importance, please refer to NextLabs’ interview with Alper Kerman, author of the Implementing a Zero Trust Architecture document, on Why is Zero Trust Architecture (ZTA) Important?


To comment on this post
Login to NextLabs Community
NextLabs seeks to provide helpful resources and easy to digest information on data-centric security related topics. To discuss and share insights on this resource with peers in the data security field, join the NextLabs community.