Home | Safeguard your Cloud
Safeguard Data in your Cloud
Adopting NextLabs Zero Trust Data-Centric Security Suite
Standing at the forefront of the intelligent enterprise evolution, hybrid and multi-cloud technologies fuel business agility and sharpen competitive edges in today’s fast-paced market. However, despite this progress, cloud security often trails behind adoption, leaving organizations lacking a unified framework to safeguard their data and assets.
According to IBM, nearly 40% of breaches led to data loss across multiple environments – public cloud, private cloud, and on-premises, with higher costs that averaged $4.75 million. Rather than remaining static, cloud security must evolve dynamically to effectively counter emerging threats and risks.
What's in the Cloud?
The cloud consists of servers accessed via the Internet, along with the software and databases that run on those servers. It enables users and companies to forego the management of physical servers or the installation of software applications on personal devices. Its ecosystem offers a wide range of services, including Infrastructure as a Service (IaaS) for virtualized computing resources, Platform as a Service (PaaS) for application development, and Software as a Service (SaaS) for accessing web-based applications.

Compute
Provides virtualized computing resources for users to run apps & perform tasks

Storage
Offers scalable options for storing and managing data on the cloud
Applications
Allow users to run and access software over the internet from cloud-hosted servers

Database
Enables users to store, manage, and analyze structured data on the cloud

Analytics
Facilitates data analysis, visualization, and insights to make informed decisions

Networking
Connects and manages resources for secure and efficient data communication

DevOps
Streamline software development, deployment, and automation processes

Mgmt. Tools
Helps users oversee and optimize cloud infrastructure and resources

Security
Protect data, apps, and infrastructure from threats and vulnerabilities

Business Services
Support business functions, such as CRM, marketing, and financial management
Key Drivers for Cloud Security
Given the wide range of services and products in the cloud, organizations are searching for an approach that secures data anywhere and everywhere. This involves the need to control and oversee access, protect data across different environments and tailor each solution according to its cloud service model.
Controlling Administrative and User Access in the Cloud
- ‘Need-to-know’ Access for Privileged Users: This approach ensures that administrators have access only to the data and resources essential for their tasks, minimizing the risk of internal threats and data breaches.
- Least Privilege Access for End Users: Granting users the minimum levels of access—or permissions—needed to perform their job functions. By limiting the scope of access for both admins and end users, organizations can significantly reduce vulnerabilities and enhance the overall security posture of their cloud environments.
Data Protection Across Hybrid and Multi-Cloud Environments
- Securing Data Beyond Network and Identity: Given the broadened attack surface and unique security protocols of each cloud environment, the strategic emphasis should be on protecting data at its core. This encompasses a comprehensive solution that secures data on-premises and across cloud platforms.
- Securing Data Throughout Its Lifecycle: As data moves into, out of, and between clouds, each flow becomes a risk vector. This calls for multi-layered security, at data access layer, application layer, exit point and file layer.
- Centralized Monitoring: Implement comprehensive monitoring by aggregating numerous logs from various access points, for visibility and control across different hybrid and multi-cloud platforms.
Choosing the Right Cloud Solution
Security Needs For Each Service Model
SaaS: Provider is responsible for delivering the software and its upkeep, while the organization is responsible for defining access control policies and proper handling of sensitive information and compliance.
PaaS: Provider offers the software and tools needed to build applications, while the organization ensures the security of data and apps.
IaaS: Provider is responsible for hosting essential infrastructure components, focusing on their physical and environmental security, while the organization is responsible for securing applications, data, and user access.
Prevent Unauthorized Access By Third-Party Admins
No matter which service model, organizations must protect their cloud data from CSP admins. Given that managing user permissions is insufficient to stop operators from viewing sensitive information, there should be extra controls such as encryption and obfuscation to prevent unauthorized disclosure of sensitive data.
Why Cloud Security Needs to be Dynamic
Given the stringent core security requirements, cloud security cannot remain static and must continuously evolve to adapt to changing technologies. Outlined below are key reasons that highlight the need for dynamic cloud security:
- Increased Data Availability: With the increased volume of data and shift towards virtualization and remote work, information is more accessible than ever, which increases the risk of data being replicated anywhere and everywhere.
- Third Party Risks: Traditional access controls are often ineffective against privileged users, who can bypass standard protections. Enhanced security measures are required to monitor these users, ensuring that their privileged status does not become a liability.
- Securing Cross-Enterprise Collaboration: Security controls must extend beyond organizational borders, managing multiple identities and access levels across complex supply chain networks while also ensuring regional compliance.
- Need for Automation: Manual responses to security threats have become impractical due to the compounded volume of data access and sharing risks. Automating cloud security reduces the need for manual intervention, enabling more consistent and reliable implementation of protective measures.
Therefore, organizations require technology that can dynamically enforce cloud security measures. One such effective method would be to adopt the Zero Trust Architecture and implement a Policy Engine that makes real-time authorizations decisions based on attribute-driven policies, which surpasses traditional static methods in adapting to business, security, and compliance requirements.
How NextLabs Safeguards Data
Anywhere in the Cloud
NextLabs’ data-centric security suite safeguards data anywhere in the cloud by enforcing access rights and protects data of all types — unstructured and structured, throughout its lifecycle whether in transit, at rest, or in use. Based on zero trust architecture, the solution offers the following core capabilities:
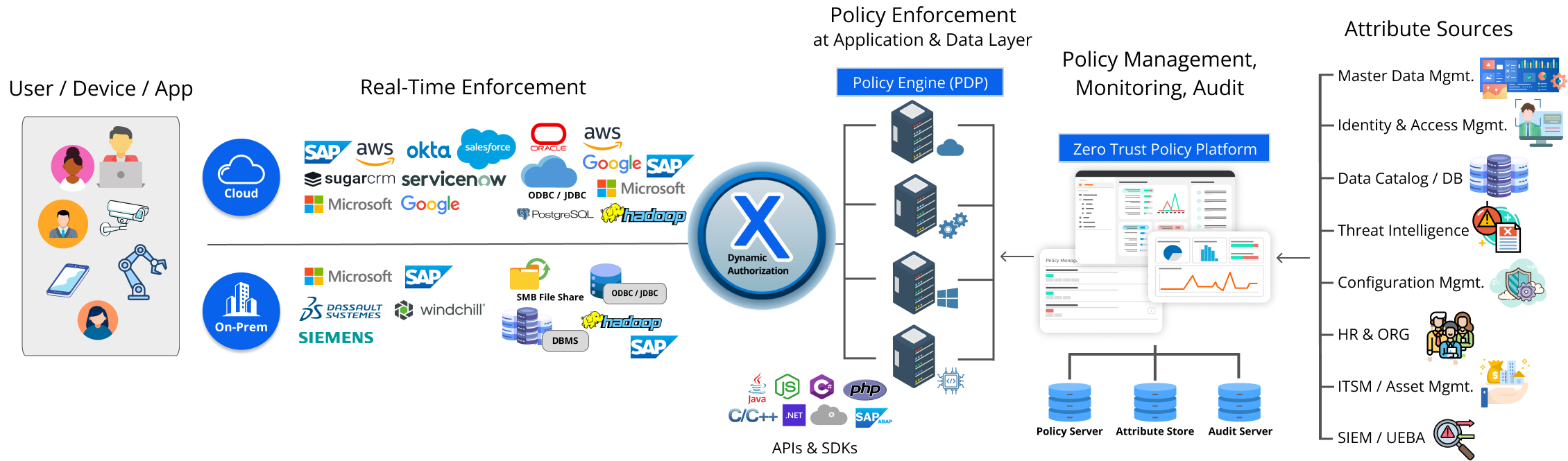
Zero Trust Policy Platform
On the policy platform, business and security needs are digitized and stored as centrally managed, attribute-based policies. Organizations can easily apply security rules to applications and documents, defining who can access what data and what actions are permissible.
Dynamic Authorization
During access attempts, the policy engine employs the Attribute-Based Access Control (ABAC) method in real-time, evaluating and authorizing access based on user, device, resource and contextual attributes. This method aligns with the 'Least Privileged Access' principle of Zero Trust Architecture, providing access rights only when necessary and re-evaluating these rights with each new request.
Real-Time Enforcement
After the policy engine evaluates an access attempt, its decision is sent to policy enforcers that implement data-centric security controls in real time. These controls range from Digital Rights Management to dynamic data masking and redaction techniques, which obscure sensitive information. This ensures the security and integrity of the data no matter who it is shared with.
Automation and Prevention
Diverging from traditional detect-and-respond models, policy enforcement allows organizations to mitigate risks before they become actual threats. This preventive strategy aims to minimize risks compared to the more resource-intensive methods of dealing with issues post-occurrence. Additionally, all data access activity is automatically logged and monitored, instantly alerting on any anomalous activity.
Zero Trust Data Security for the Cloud
NextLabs Zero Trust Data Security is a comprehensive suite of access enforcement and data protection applications powered by CloudAz, a zero trust policy platform. It consists of policy enforcers (Application Enforcer, SkyDRM, and Data Access Enforcer) to proactively prevent unauthorized access of data across applications, file repositories and databases, even in compromised systems.
NextLabs can be deployed anywhere, be it on-premises, in private cloud, or as a SaaS. Running natively on AWS, Azure, OpenShift and Google Cloud, the Suite offers organizations the freedom to choose the right cloud deployment strategy, whether it is hybrid or multi-cloud. Policies can be transported between cloud and on-premises deployments, ensuring consistent policy enforcement across all environments.
SaaS

Private Cloud

On-Premise
CloudAz
CloudAz is a centralized policy management platform with real-time enforcement that centralizes administration and employs a zero trust principle to enforce data-centric security measures and compliance in real-time. Its containerized architecture supports both Kubernetes-based and non-Kubernetes based cloud platforms to allow for seamless deployment. CloudAz runs natively on AWS, Azure, OpenShift and Google Cloud.
SkyDRM
SkyDRM provides persistent protection of unstructured data at rest and in transit, regardless of where it exists. It integrates with SaaS applications such as OneDrive, Google Drive, and Dropbox to protect sensitive documents stored in the cloud. Users can automate rights protection, view protected documents and share protected documents easily and securely within SaaS applications.
Application Enforcer
Application Enforcer simplifies access management and uses ABAC to enforce the principle of least privilege, ensuring apps and data are accessed only by authorized entities. It works natively with leading enterprise apps, such as Microsoft Dynamics 365, ServiceNow, Salesforce and Slack, externalizing authorization and providing an extra layer of controls all without the need for custom coding.
Data Access Enforcer (DAE)
NextLabs Data Access Enforcer for Microsoft and Azure SQL (DAE for Microsoft and Azure SQL) provides dynamic data-level security controls and fine-grained data access governance for both Microsoft SQL and Azure SQL. DAE for Microsoft and Azure SQL enforces data-level security controls - such as field-level data masking and record level data segregation and monitors data access activity directly from within the data access layer.
Adopting NextLabs Suite

For an organization to adopt the best cloud security practices of an intelligent enterprise, it must implement data-centric security with zero trust architecture. Learn how NextLabs facilitates this transformation below:

-
Policy-Driven Intelligent EnterprisePolicy-Driven Intelligent Enterprise

-
Data-Centric SecurityData-Centric Security

-
Zero Trust ArchitectureZero Trust Architecture


